What is a Web Application?
Before discussing what constitutes a web application attack, let us first look at what is a web application or widget.
Over the past decade or so, the web has been embraced by millions of businesses as an inexpensive channel to communicate and exchange information with prospects and transactions with customers. In particular, the web provides a way for marketers to get to know the people visiting their sites and start communicating with them. One way of doing this is by asking web visitors to subscribe to newsletters, to submit an application form when requesting information on products, or provide details to customize their browsing experience when next visiting a particular website.
The web is also an excellent sales channel for a myriad of organizations, large or small: with over 1 billion Internet users (source: Computer Industry Almanac, 2006), US e-commerce spending accounted for $102.1 billion in 2006 (Source: comScore Networks, 2007). All this data must be somehow captured, stored, processed and transmitted to be used immediately or at a later date. Web applications, in the form of submit fields, inquiry, and login forms, shopping carts, and content management systems, are those website widgets that allow this to happen. They are, therefore, fundamental to businesses for leveraging their online presence thus creating long-lasting and profitable relationships with prospects and customers.
No wonder web applications have become such a ubiquitous phenomenon. However, due to their highly technical and complex nature, web applications are a widely unknown and a grossly misunderstood fixture in our everyday cyber-life.
Web Applications Defined
From a technical viewpoint, the web is a highly programmable environment that allows mass customization through the immediate deployment of a large and diverse range of applications to millions of global users. Two important components of a modern website are flexible web browsers and web applications; both available to all and sundry at no expense.
Web browsers are software applications that allow users to retrieve data and interact with content located on web pages within a website. Today’s websites are a far cry from the static text and graphics showcases of the early and mid-nineties: modern web pages allow personalized dynamic content to be pulled down by users according to individual preferences and settings. Furthermore, web pages may also run client-side scripts that change the Internet browser into an interface for such applications as webmail and interactive mapping software (e.g., Yahoo Mail and Google Maps).
Most importantly, modern web sites allow the capture, processing, storage and transmission of sensitive customer data (e.g., personal details, credit card numbers, social security information, etc.) for immediate and recurrent use. And this is done through web applications. Such features as webmail, login pages, support and product request forms, shopping carts, and content management systems shape modern websites and provide businesses with the means necessary to communicate with prospects and customers. These are all common examples of web applications.
Web applications are, therefore, computer programs allowing website visitors to submit and retrieve data to/from a database over the Internet using their preferred web browser. The data is then presented to the user within their browser as information is generated dynamically (in a specific format, e.g. in HTML using CSS) by the web application through a web server.
For the more technically oriented, web applications query the content server (essentially a content repository database) and dynamically generate web documents to serve to the client (people surfing the website). The documents are generated in a standard format to allow support by all browsers (e.g., HTML or XHTML). JavaScript is one form of client-side script that permits dynamic elements on each page (e.g. an image changes once the user hovers over it with a mouse). The web browser is key – it interprets and runs all scripts etc. while displaying the requested pages and content. Wikipedia brilliantly terms the web browser as the universal client for any web application.
Another significant advantage of building and maintaining web applications is that they perform their function irrespective of the operating system and browsers running client-side. Web applications are quickly deployed anywhere at no cost and without any installation requirements (almost) at the user’s end.
As the number of businesses embracing the benefits of doing business over the web increases, so will the use of web applications and other related technologies continue to grow. Moreover, since the increasing adoption of intranets and extranets, web applications become greatly entrenched in any organization’s communication infrastructures, further broadening their scope and possibility of technological complexity and prowess.
Web applications may either be purchased off-the-shelf or created in-house.
How Do Web Applications Work?
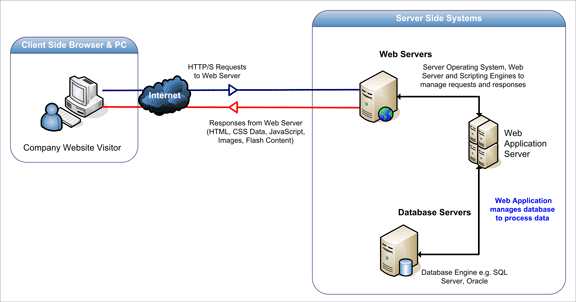
The figure below details the three-layered web application model. The first layer is normally a web browser or the user interface; the second layer is the dynamic content generation technology tool such as Java servlets (JSP) or Active Server Pages (ASP), and the third layer is the database containing content (e.g., news) and customer data (e.g., usernames and passwords, social security numbers, and credit card details).
The figure below shows how the initial request is triggered by the user through the browser over the Internet to the web application server. The web application accesses the databases servers to perform the requested task updating and retrieving the information lying within the database. The web application then presents the information to the user through the browser.
What is a Web Application Attack
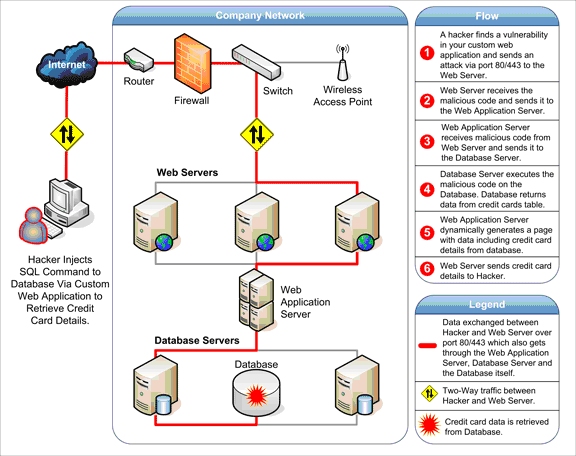
Let us now look at types of attacks on web applications. Despite their advantages, web applications do raise a number of security concerns stemming from improper coding. Serious weaknesses or vulnerabilities allow criminals to gain direct and public access to databases in order to churn sensitive data – this is known as a web application attack. Many of these databases contain valuable information (e.g. personal data and financial details) making them a frequent target of attacks. Although such acts of vandalism (often performed by the so-called script kiddies) as defacing corporate websites are still commonplace, nowadays attackers prefer gaining access to the sensitive data residing on the database server because of the immense pay-offs in selling the results of data breaches. In the framework described above, it is easy to see how a criminal can quickly access the data residing on the database through a dose of creativity and, with luck, negligence or human error, leading to vulnerabilities in the web applications.
As stated, websites depend on databases to deliver the required information to visitors. If web applications are not secure, i.e. vulnerable to at least one of the various forms of hacking techniques, then your entire database of sensitive information is at serious risk of a web application attack. SQL Injection attack types, which target the databases directly, are still the most common and the most dangerous type of vulnerability. Other attackers may inject malicious code using the user input of vulnerable web applications to trick users and redirect them towards phishing sites. This type of attack is called Cross-Site Scripting (XSS attacks) and may be used even though the web servers and database engine contain no vulnerability themselves. It is often used in combination with other attack vectors such as social engineering attacks. There are many other types of common attacks such as directory traversal, local file inclusion, and more.
Recent research shows that 75% of cyber attacks are done at the web application level.
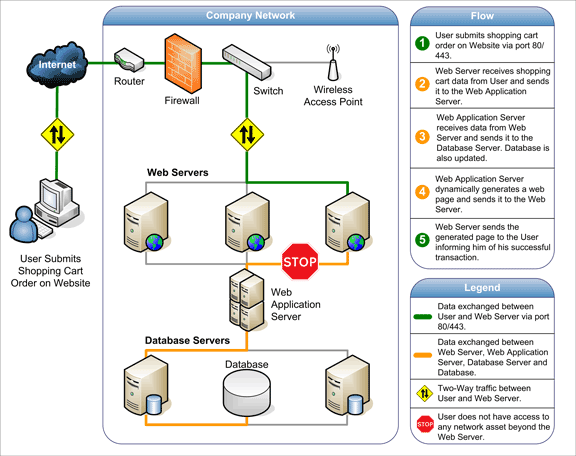
- Websites and related web applications must be available 24 hours a day, 7 days a week, to provide the required service to customers, employees, suppliers, and other stakeholders.
- Firewalls and SSL provide no protection against a web application attack, simply because access to the website has to be made public. All modern database systems (e.g. Microsoft SQL Server, Oracle, and MySQL) may be accessed through specific ports (e.g., port 80 and 443) and anyone can attempt direct connections to the databases effectively bypassing the security mechanisms used by the operating system. These ports remain open to allow communication with legitimate traffic and therefore constitute a major vulnerability.
- Web applications often have direct access to backend data such as customer databases and, hence, control valuable data and are much more difficult to secure. Those that do not have access will have some form of script that allows data capture and transmission. If an attacker becomes aware of weaknesses in such a script, they may easily reroute unwitting traffic to another location and illegitimately hive off personal details.
- Most web applications are custom-made and, therefore, involve a lesser degree of testing than off-the-shelf software. Consequently, custom applications are more susceptible to attack.
Web applications, therefore, are a gateway to databases especially custom applications which are not developed with security best practices and which do not undergo regular security audits. In general, you need to answer the question: “Which parts of a website we thought secure, is open to a web application attack?” and “what data can we throw at an application to cause it to perform something it shouldn’t do?”.
This is the work of a web vulnerability scanner.
Types of Web Application Attacks
1. Injection Attacks
- SQL Injection (SQLi) – Attackers inject malicious SQL queries to manipulate databases.
- Command Injection – Executing arbitrary system commands on the server.
- LDAP Injection – Injecting malicious LDAP queries to bypass authentication.
- NoSQL Injection – Attacking NoSQL databases like MongoDB.
2. Cross-Site Attacks
- Cross-Site Scripting (XSS) – Injecting malicious scripts into webpages viewed by users.
- Cross-Site Request Forgery (CSRF/XSRF) – Forcing users to perform unintended actions on a website.
3. Authentication & Session Attacks
- Credential Stuffing – Using leaked username/password combinations.
- Brute Force Attack – Trying multiple password combinations.
- Session Hijacking – Stealing session tokens to impersonate users.
- Session Fixation – Tricking users into using a known session ID.
4. Broken Access Control
- Privilege Escalation – Gaining unauthorized admin or higher privileges.
- Insecure Direct Object References (IDOR) – Accessing data by manipulating parameters.
5. Security Misconfigurations
- Default Credentials – Using weak or unchanged default usernames/passwords.
- Exposed Debugging & Error Messages – Leaking sensitive info in error responses.
6. Data Exposure & Leaks
- Unencrypted Data (Sensitive Data Exposure) – Storing or transmitting unencrypted sensitive data.
- Directory Listing Exposure – Allowing attackers to browse directories.
7. Denial-of-Service (DoS) & Distributed DoS (DDoS)
- HTTP Flood Attack – Overloading a server with excessive HTTP requests.
- Slowloris Attack – Holding server connections open to exhaust resources.
8. Supply Chain Attacks
- Dependency Confusion – Tricking apps into using malicious third-party packages.
- Malicious NPM/PyPI Packages – Injecting malware into widely used libraries.
9. Clickjacking
- Trick users into clicking hidden elements (e.g., invisible login/logout buttons).
10. Server-Side Request Forgery (SSRF)
- Exploiting a server to send requests to internal systems.
11. WebSocket Attacks
- Exploiting insecure WebSocket connections to hijack user sessions or data.
12. API Security Vulnerabilities
- Insecure API Keys – Exposing API credentials.
- Improper Rate Limiting – Allowing abuse through excessive API calls.
13. Business Logic Attacks
- Manipulating workflows (e.g., price manipulation in e-commerce).
Acunetix
Proof of such exploits are readily available on the Internet and are the subject of discussion in several press releases by Acunetix, a leading vendor of web application security products. To check whether your website is vulnerable to web application attacks, get the Acunetix demo.
Frequently asked questions
A web application is an application that runs on a web server and users access it using a web browser. You could say that it is a complex dynamic website. Web applications often deliver content from a database based on what the user selects. They often do a lot of processing on the side of the browser, not the server. Web applications used to be called widgets.
Read about the basics of website and web application security.
Web applications can be attacked because their creators make errors that allow unauthorized people to access sensitive data or gain administrative access rights to the web application itself or even to the server. Attacks usually exploit the fact that web applications accept user input and this input may not be screened for malicious content.
Learn about the basic principles of secure coding, which helps avoid web application vulnerabilities.
Web applications are very vulnerable to attacks because, by design, they cannot be protected by firewalls. They must be available to everyone, all the time, unless they are on an intranet. Malicious hackers can, therefore, try to exploit them easily.
See a step-by-step example of an advanced attack on a web application.
There are two ways to protect against web application attacks. The best way is to find and eliminate all vulnerabilities. You can do it manually, which requires hiring specialists, but you can also use a professional scanner like Acunetix. The second method of protection is web application firewalls but they do not eliminate problems and can be bypassed by attackers.
Find out how Acunetix Premium can help you protect your web applications.