What is HIPAA Compliance?
The Health Insurance Portability and Accountability Act (HIPAA) was enacted by the U.S. Congress in 1996. The Act is massive in scope with five separate Titles. Title II of HIPAA, known as the Administrative Simplification provisions, requires the establishment of national standards for electronic health care transactions and national identifiers for providers, health insurance plans, and employers. The Administrative Simplification provisions also address the security and privacy of health data. The HIPAA rules and standards are meant to improve the efficiency and effectiveness of America’s health care system by encouraging the widespread use of electronic data interchange.
Who do HIPAA Rules apply to?
HIPAA standard requirements apply to 1) A health plan, 2) A health care clearinghouse, 3) A health care provider who transmits any data in electronic form. In short, any healthcare company or organisation that holds patient information.
Which sections refer to web security?
In terms of electronic security, one of the most important sections is 164.312 (a) (1) which requires entities to implement procedures to maintain information systems preventing unauthorised access. This would include preventing cyber criminals from accessing the information remotely by gaining access through a web-facing server.
164.312 (a) (1) Standard: Access control. Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights as specified in §164.308(a)(4).
While the act does not specify what measures must be taken, it does place full responsibility on the entity holding the information. Therefore it is up to the company or organisation to implement an appropriate procedure for maintaining the security of the patient information.
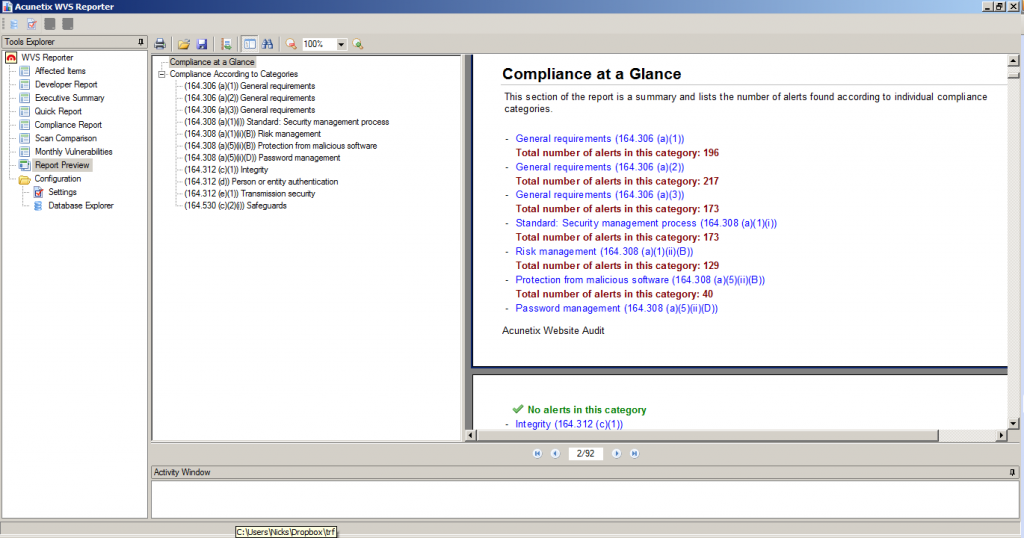
Other elements of the HIPAA rules standards which would also be applicable are 164.306 (a) (1-3) and 164.308 (a) (1) and (5). These are more generalised elements which refer to security and safeguards, which of course would be relevant to 164.312 (a) (1) as not allowing unauthorised access to records is essential to security and safeguarding of information.
Below see the relevant sections of 164.306 and 164.308 in full.
§164.306 Security standards: General rules.
(a) General requirements. Covered entities and business associates must do the following:
(1) Ensure the confidentiality, integrity, and availability of all electronic protected health information the covered entity or business associate creates, receives, maintains, or transmits.
(2) Protect against any reasonably anticipated threats or hazards to the security or integrity of such information.
(3) Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required under subpart E of this part.
‘HIPAA §164.308 Administrative safeguards.
(a) A covered entity or business associate must, in accordance with §164.306:
(1) (i) Standard: Security management process. Implement policies and procedures to prevent, detect, contain, and correct security violations.
(ii) Implementation specifications:
(B) Risk management (Required). Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with §164.306(a).
(5) (ii) Implementation specifications. Implement:
(B) Protection from malicious software (Addressable). Procedures for guarding against, detecting, and reporting malicious software.
(D) Password management (Addressable). Procedures for creating, changing, and safeguarding passwords.’
How can I make sure my web application is compliant with the HIPAA rules?
The most straightforward method for meeting this standard would be to first check if any weaknesses currently exist in the web applications owned by the company or organisation. This is usually done using a tool known as a web vulnerability scanner. This is a complex tool which automatically scans the web application to look for security issues. Some of the most common of these are SQL Injection, Cross Site Scripting and Denial of Service vulnerabilities. Each type of vulnerability has many variants and therefore it’s important to have extremely thorough checks in place for the most common routes of attack. Further manual checks should also be undertaken by a security professional.
In the case of data theft, SQL Injection is the most likely method of attack; basically the web application would be tricked into releasing confidential data such as patient records. Such information is becoming even more valuable to hackers than financial records as it can be used for identity theft, blackmail purposes, theft of intellectual property and any other deviant act imaginable. Whereas financial institutions have long been aware of threats and have sophisticated security measures in place, other holders of personal information such as medical insurance companies have not yet adapted.
So, it’s vital that any vulnerabilities are detected, which will then allow the web application manager to fix these at code level. Once this has taken place, the application should be scanned regularly to identify any new vulnerabilities and a web application firewall put in place as an added line of defense.
Keeping on top of the latest methods used by cybercriminals and closing any potential routes of exploitation will keep patient information secure from cyber attacks.
One such scanner for this purpose is Acunetix, which is particularly effective for identifying SQL Injection and Cross Site Scripting vulnerabilities. Acunetix was developed around the same time as HIPAA came into place, therefore has evolved with those needs in mind. There is even a specific report within Acunetix to identify and detail which elements of the HIPAA rules a web application is not complying with, detailing the type of vulnerability found, it’s location in the web application architecture and how to fix it. Read more about Acunetix Regulatory Compliance Reports.