A simple web vulnerability scanner is not enough for a business to maintain web application security. Businesses require solutions that treat web security vulnerabilities as processes, not as one-time events (just like in the case of anti-malware solutions). That is why a business-oriented solution must include not only vulnerability scanning but also vulnerability assessment and vulnerability management functionality. No matter whether you need to secure your in-house development, for example, PHP or Java applications, or third-party tools, such as WordPress and its plugins, you need the best tool for the job.
Acunetix is available on-premise for the Windows and Linux operating systems as well as an online service giving you greater flexibility when it comes to web application vulnerability scanning.
Top-of-the-Line Vulnerability Scanning
There are certain qualities that a business-oriented vulnerability scanner must possess. It must find as many security holes as possible and be able to find them quickly. Additionally, the security scanner must not hinder the operations by reporting false positives.
- The Acunetix scanning engine is developed using very efficient technologies. It handles even complex web applications, which use a lot of HTML5 and JavaScript. It also works very quickly in real-time and covers a full range of security vulnerabilities including OWASP Top 10 categories: from SQL Injections and Cross-site Scripting (XSS) to web server misconfigurations and other configuration issues.
- The rate of false-positive reporting is very low for the Acunetix security tool. Optionally, if you use its IAST module, AcuSensor, it reduces the rate even further.
Best-in-Class Vulnerability Assessment Functionality
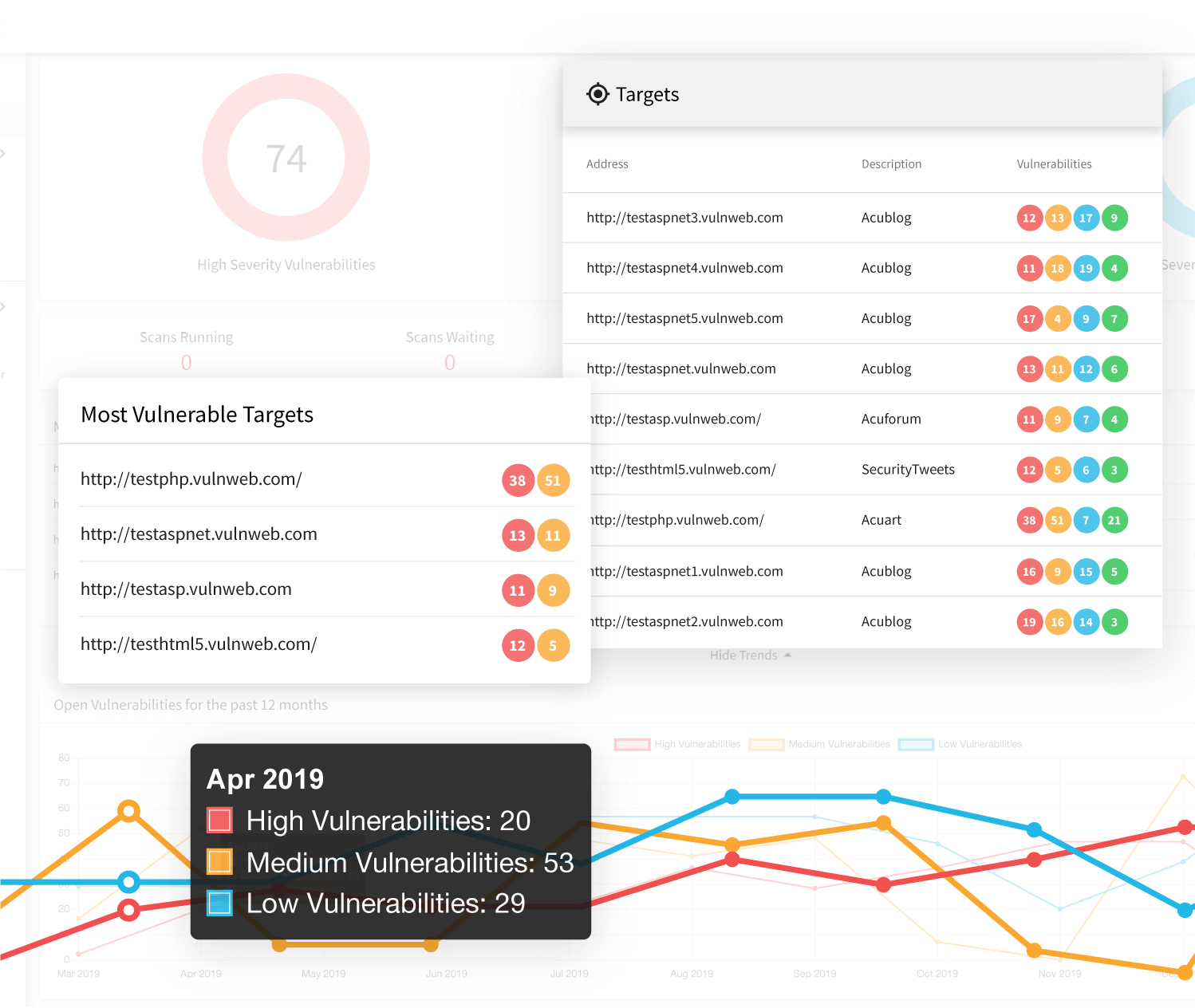
After a security vulnerability is found, there is a need for security assessment which includes classifying the vulnerability according to potential security risks. Acunetix is also a vulnerability assessment tool. It provides businesses with information, which helps prioritize security patches.
- Each discovered new vulnerability is classified according to renowned cybersecurity classification schemes and presented along with detailed information useful for further penetration testing as well as patching advice.
- Application vulnerabilities are assigned one of four severity ratings based on their potential impact on the business and the ease of exploit.
- The Acunetix reporting engine provides detailed vulnerability assessment reports for further analysis.

Vulnerability Management: Vulnerabilities as Processes
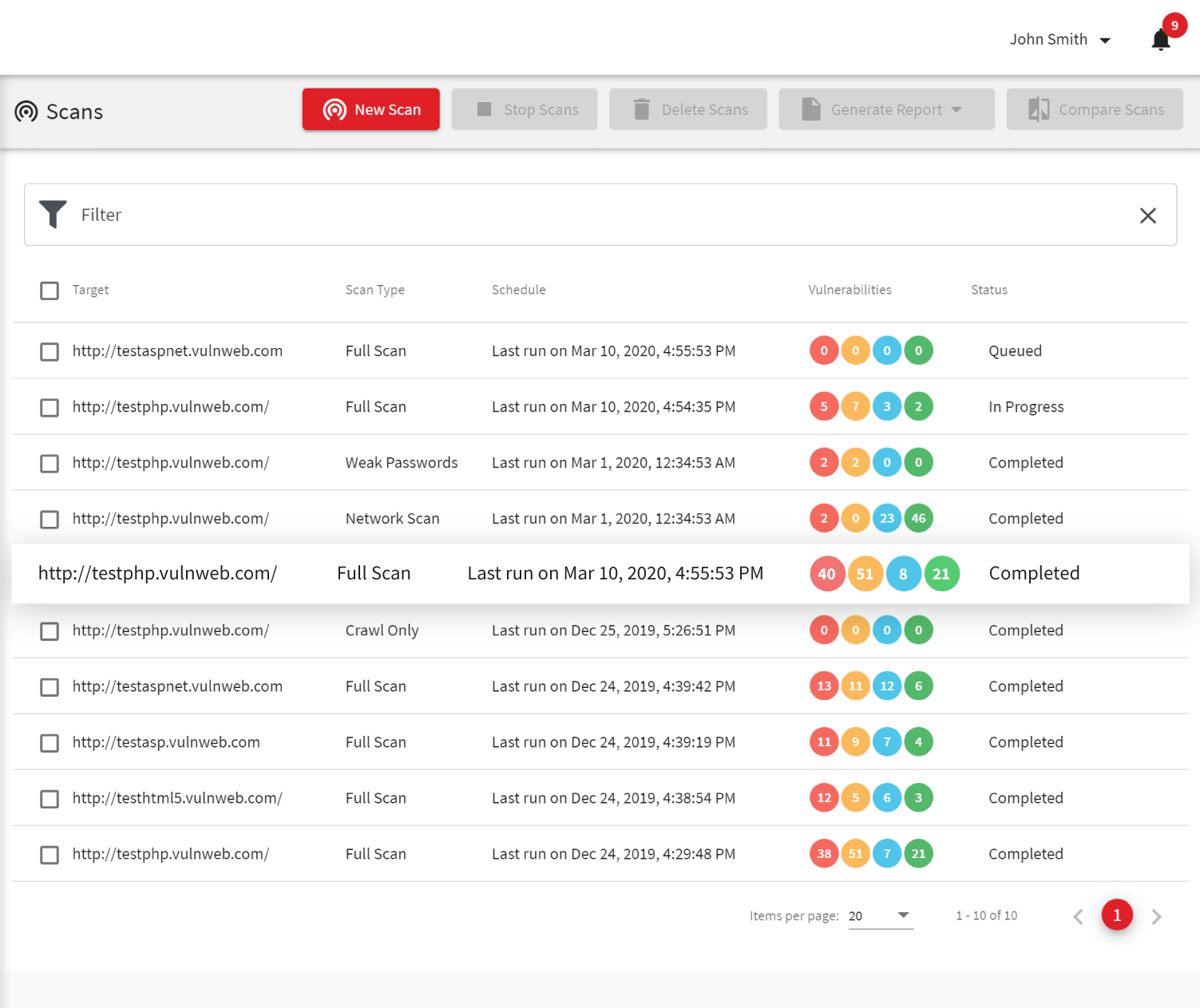
Finding a vulnerability and assessing its severity is an automatic process, which takes very little time. After this is completed, the most time-consuming and complex process starts – fixing the vulnerability and verifying the fix. If this process needs to be handled manually, it requires a lot of resources and the risk of making mistakes is high. That is why Acunetix makes it easy to automate it as much as possible.
- Acunetix works with leading issue management solutions. It can automatically create issues. This way the manual part of the issue management process is limited to the issue management solution.
- If you develop your web applications in-house, you need to check them for potential security issues as soon as possible. Acunetix works with CI/CD solutions that build and run your web applications in virtual environments.
- A vulnerability may resurface after some time and it’s valuable to know the original one. This may speed up the patching process considerably. Acunetix facilitates this, as well.

We utilize Acunetix to more thoroughly assess internet-facing websites and servers. Acunetix helps us identify vulnerabilities in conjunction with other vulnerability scanning applications. Acunetix has been a more reliable application when discovering / determining different types of malicious code injection vulnerabilities (SQL, HTML, CGI, etc).