PHP Security Scanner – Enter Acunetix!
PHP security vulnerabilities are a major cause for concern when it comes to web applications written in the PHP language since successful exploitation of such security flaws may lead to several commonly exploited attacks.
Many vulnerabilities are usually not difficult to fix, but finding them in large codebases could be challenging without the right tools. Acunetix is a web application vulnerability scanner that automatically tests web applications for SQL Injection, Cross-site Scripting (XSS), Local File Inclusion, LDAP injection and a plethora of other security issues.
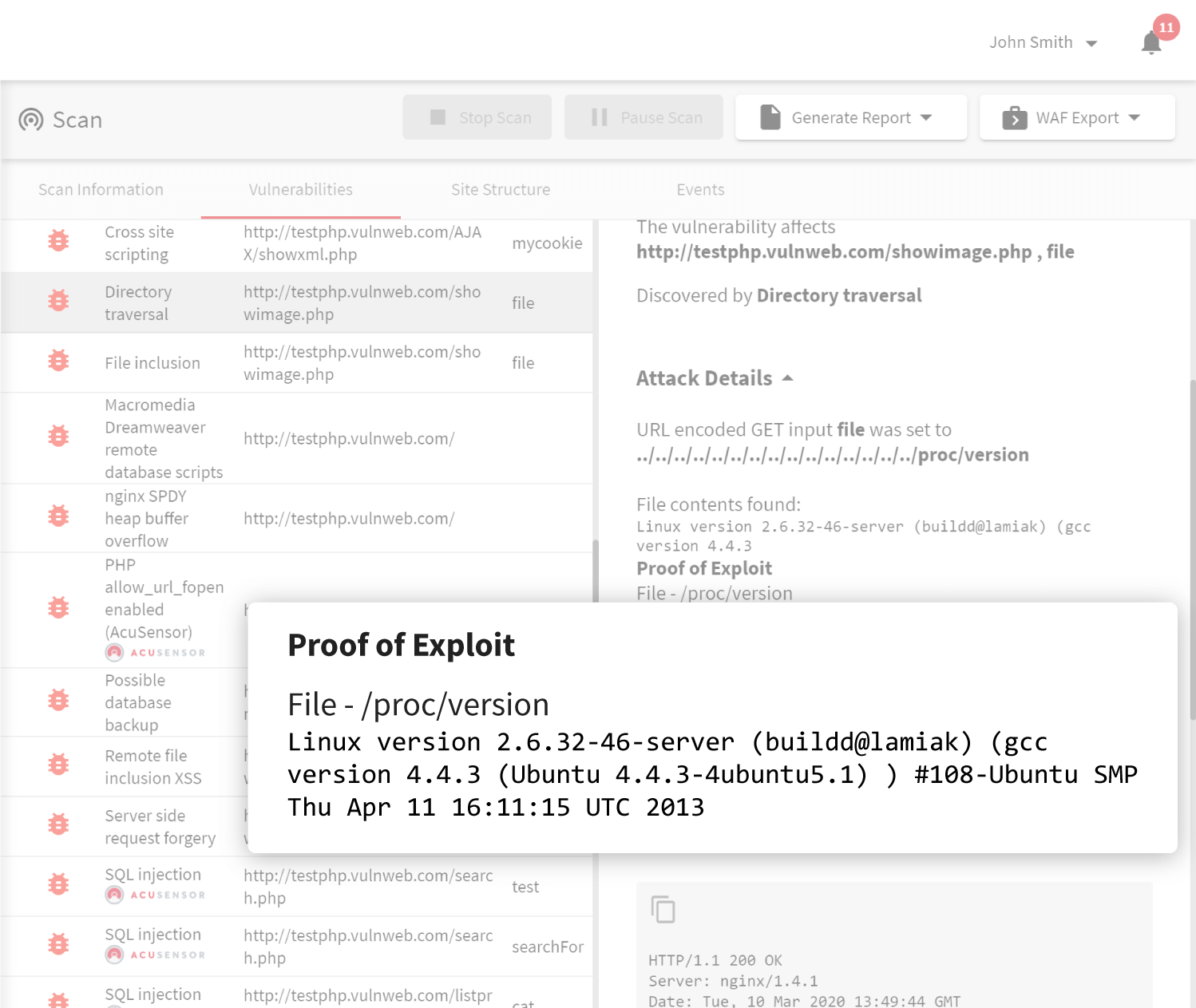
Beyond Low Hanging Fruit
The Acunetix web application security scanner can scan for a myriad of security vulnerabilities and goes well beyond basic security tests may other scanners typically perform, all while keeping false positives to an absolute minimum.
This in part is thanks to the advanced crawler and JavaScript engine called DeepScan. Acunetix DeepScan brings full support for modern single-page applications (SPAs) and can understand and fully test applications that rely on JavaScript frameworks like React, Angular, Ember, and Vue. Acunetix can also detect hard to find DOM based Cross-site Scripting using advanced taint analysis techniques.
Beyond all of this, Acunetix can also detect known vulnerabilities in PHP scripts and other open-source projects such as vulnerable WordPress plugins.
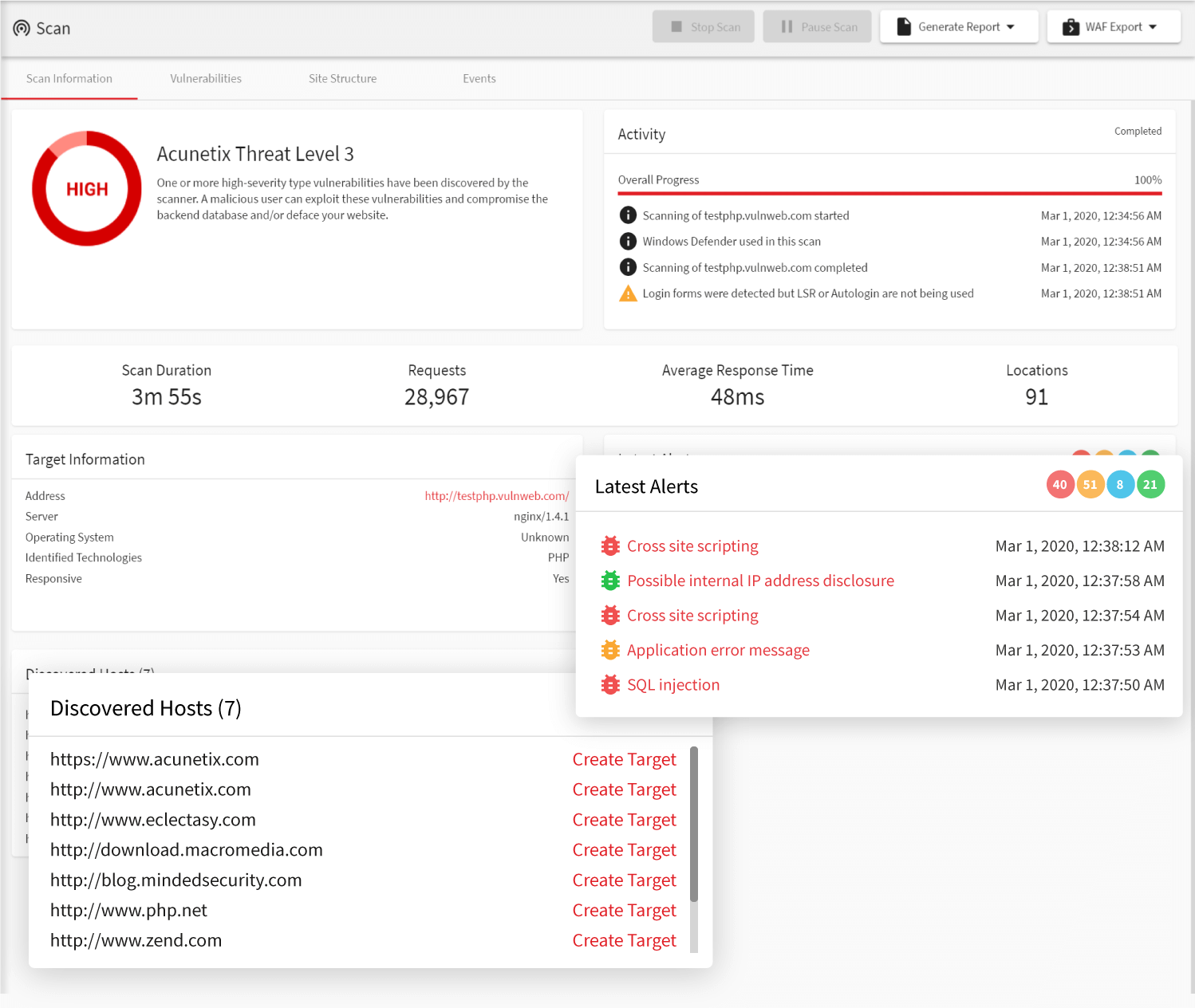
Runtime PHP Source Code Analysis
In addition to being a fully automated black-box scanner (uses HTTP without any access to the PHP code), Acunetix also provides AcuSensor as part of its standard offering. AcuSensor is a an optional sensor for PHP applications (also available for Java and ASP.NET) that can easily be deployed on the application webserver backend to analyze the source code while it is in execution by the scanner.
This type of testing is known as gray-box testing since it combines the best of both worlds from black-box testing and white-box (static source code analysis) testing. When testing for file inclusion vulnerabilities, Acunetix AcuSensor increases the accuracy of a scan since it has access to the code at the back end. With AcuSensor, Acunetix can also test pages that would not otherwise be discovered via crawling thanks to AcuSensor’s back-end crawl technology.

Simple Reporting and Issue Tracker Integration
Another issue that Acunetix solves over some other scanning tools is the ability to instantly generate a wide variety of technical, regulatory, and compliance reports such as PCI DSS, HIPAA, OWASP Top 10, and many others.
Additionally, Acunetix allows users to export discovered vulnerabilities to issue trackers such as Atlassian Jira, GitHub, GitLab, Bugzilla, Mantis, and Microsoft Team Foundation Server (TFS). Additionally, if you use Jenkins as your continuous integration tool, Acunetix can even directly integrate with it.
Frequently asked questions
SAST (Static Application Security Testing) is used to analyze the security of the source code, for example, PHP code. However, such tools miss out on a lot of vulnerabilities and therefore should always be paired with a DAST tool (Dynamic Application Security Testing) – a web vulnerability scanner such as Acunetix.
SAST (Static Application Security Testing) tools require access to the source code and must be written for a specific language, for example PHP; they often report a lot of false positives and they are unable to find issues such as misconfigurations. DAST (Dynamic Application Security Testing) tools such as Acunetix don’t need access to the source code and can work with any programming language; they report few false positives and can find a lot more issues than SAST tools.
Read more why DAST is recommended as the basis for web security.
Acunetix can be used to verify the security of PHP applications as a DAST tool or as an IAST tool. When used as a DAST tool, it requires no access to the back-end at all. Acunetix AcuSensor is an IAST sensor for PHP (and other languages) that gives you insight into the source code but you do not need to modify the code to use it.
To write secure PHP code, make sure to always assume that any user input may be malicious. Sanitize all user input by filtering (using whitelists rather than blacklists) and escaping as appropriate. Also make sure to use modern PHP functions and methods that are designed to be secure, for example, prepared statements for SQL.
Click here to learn how to avoid SQL Injection vulnerabilities in PHP.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox