Fast and Flexible Compliance
With application security risks evolving so quickly, modern software security is full of complexities. As such, many legacy vulnerability scanners designed to scan websites built a decade ago can’t properly scan large and complex web applications quickly and accurately without security experts on staff. With a re-engineered core and a highly optimized crawler, every inch of Acunetix is tuned for speed, efficiency, and accuracy, allowing it to find vulnerabilities even in the largest and most complex of applications without breaking a sweat. What’s more, with Acunetix, it’s possible to throttle the speed at which a scan runs, ensuring that even high-traffic sites can be scanned without affecting their performance. You can also schedule compliance scans to run at specific times of a day, week, or month, or even define your own custom schedule. You also have the option of running scans on a continuous basis with Acunetix, only running a quick scan every day of the week, with a full compliance scan run once a week. This ensures that any new vulnerabilities that may have been introduced in-between full scans get picked up by Acunetix immediately.
Beyond the OWASP Top 10
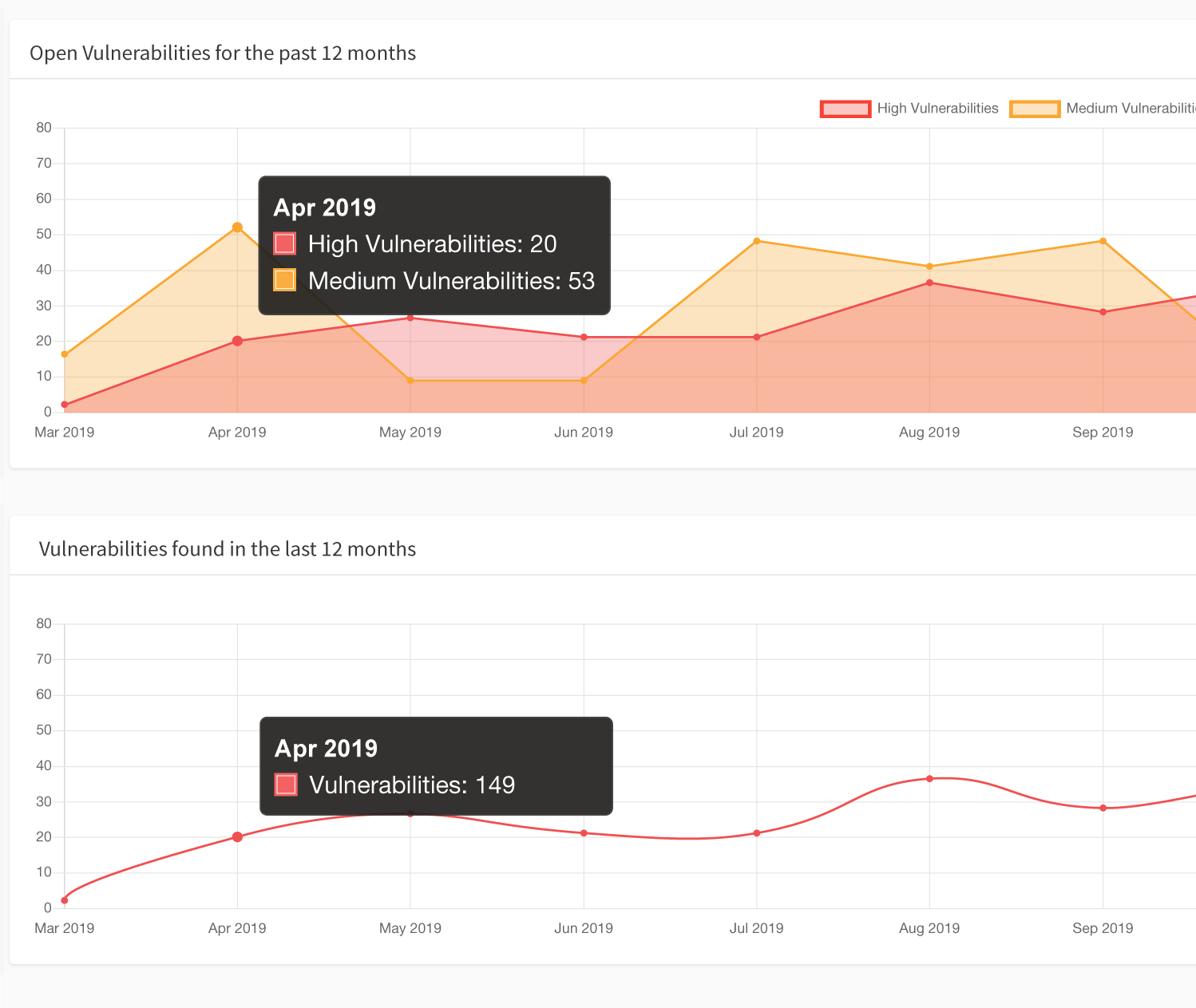
Another problem that Acunetix solves, which many other external vulnerability scanners fall short of, is the ability to produce great reports. While Acunetix can provide you with an OWASP Top 10 compliance report, it doesn’t stop there. In addition to OWASP Top 10 compliance reports, Acunetix can also instantly generate a wide variety of other technical, regulatory, and compliance reports such as PCI DSS, NIST, and many others. Additionally, Acunetix also allows users to export discovered vulnerabilities to issue trackers such as Atlassian Jira, GitHub, GitLab, Mantis, Bugzilla, and Microsoft Team Foundation Server (TFS). One of the biggest issues with conventional web vulnerability scanners is that they simply report a list of vulnerabilities after a scan is complete. Acunetix takes a different approach in that once a vulnerability is found during a scan, it is automatically cataloged and assigned a status of Open. After the vulnerability gets fixed, Acunetix may be used to retest the vulnerability to make sure it’s properly fixed, and then automatically marks it as Fixed. All of this information is available at a glance in the Acunetix dashboard and thanks to multi-user, multi-role capabilities, security teams and other external security professionals can access exactly what they’re meant to.Frequently asked questions
OWASP Top 10 is an open report prepared every four years by the OWASP Foundation (Open Web Application Security Project). This report contains a list of security risks that are most critical to web applications.
OWASP Top 10 vulnerabilities are different in every report. The latest report lists the following: injections, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, Cross-site Scripting, insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
See the vulnerabilities listed in the annual Acunetix web application vulnerability report.
OWASP Top 10 compliance measures the presence of OWASP Top 10 vulnerabilities in a web application. It is not a formal requirement like HIPAA or PCI DSS, but it is considered the best general measure of web application security for any business. Therefore, every vulnerability scanner should have an OWASP Top 10 compliance report available.
You can find most OWASP Top 10 vulnerabilities using Acunetix. However, some OWASP Top 10 categories include business logic vulnerabilities that you may only find through manual penetration testing – no vulnerability scanners and no other automated tools can find them. Therefore, to attain full compliance, you must start with vulnerability scanning and follow up with manual penetration testing.
Read more about vulnerability scanning and penetration testing.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox