Quick and Easy HIPAA Vulnerability Compliance
With web technologies moving at such a rapid pace, modern websites are full of complexities. To such an extent, many legacy vulnerability scanners designed to scan websites built a decade ago don’t meet the needs of the modern web and therefore can’t scan large and complex web applications quickly and accurately. With a re-engineered core and a highly optimized crawler, every inch of Acunetix is tuned for speed, efficiency, and accuracy, allowing you to meet HIPAA regulations even in the largest and most complex of web applications without breaking a sweat or needing security experts on staff. What’s more, with Acunetix vulnerability scanner, it’s possible to throttle the speed at which a scan runs, ensuring that even high-traffic sites can be scanned without affecting their performance. You can also schedule HIPAA vulnerability compliance scans to run at specific times of a day, week, or month, or even define you own custom schedule. You also have the option of running scans on continuous basis with Acunetix only running a high-level scan every day of the week, with a full HIPAA compliance scan run once a week. This ensures that any new vulnerabilities that may have been introduced in-between full scans get picked up by Acunetix immediately.
Audit-Ready HIPAA Compliance Reports
With built-in reports for HIPAA and other common compliance standards such as PCI DSS, Acunetix enables you to quickly and easily conduct daily security reviews, satisfy management and auditor requests, and protect your organization against costly penalties. Additionally, Acunetix also allows users to export discovered vulnerabilities to issue trackers such as Atlassian Jira, GitHub, GitLab, Mantis, Bugzilla, and Microsoft Team Foundation Server (TFS). One of the biggest issues with conventional web vulnerability scanners is that they simply report a list of vulnerabilities after a scan is complete. Acunetix takes a different approach in that once a vulnerability is found during a scan, it is automatically cataloged and assigned a status of Open. After the vulnerability gets fixed, Acunetix may be used to re-test the vulnerability to make sure it’s properly fixed, and then automatically marks it as Fixed, allowing you to easily and accurately report on remediation progress to management, auditors, and other stakeholders quickly, accurately and, most importantly, from one centralized location. All of this information is available at a glance in the Acunetix dashboard and thanks to multi-user, multi-role capabilities, users can only see what they’re meant to. With Acunetix, you will be able to focus on web security instead of needing to become a compliance expert.Frequently asked questions
Health Insurance Portability and Accountability Act (HIPAA) is a US government act that came into force in 1996. One of the main reasons for this act was to help protect Personally Identifiable Information (PII) in healthcare from fraud and theft. In 2003, the final Security Rule was added to the act, which includes the requirement for technical safeguards of healthcare PII.
HIPAA applies to US healthcare organizations that store and transmit any health data electronically. The act includes a definition of HIPAA covered entities (45 CFR 160.103) that must be HIPAA-compliant or face penalties. HIPAA audits are conducted periodically by the Department of Health and Human Services’ Office for Civil Rights (OCR).
The HIPAA security rule does not specifically mention vulnerability scans or penetration tests. However, to comply with the security rule, Health and Human Services require a technical vulnerability assessment of all the IT assets, including all web and network assets. Therefore, to comply with HIPAA, you must regularly use a vulnerability scanner to assess the security of your assets.
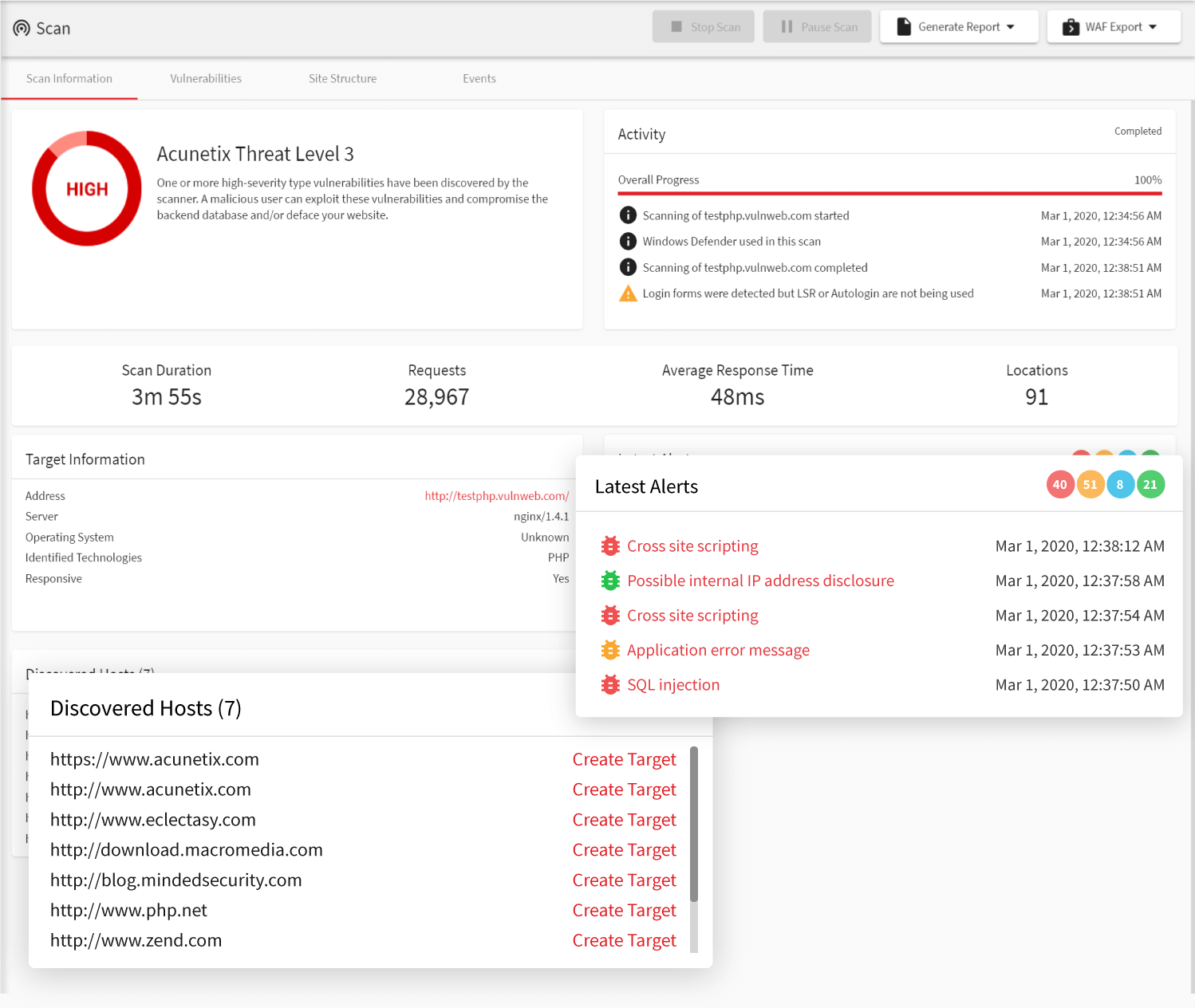
The Acunetix HIPAA report is a valuable tool for assessing the compliance of your web security measures continuously. This report organizes issues discovered by Acunetix according to HIPAA classification. The HIPAA report is available as a standard Acunetix report along with many other types of compliance reports.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox