Acunetix Free Manual Pen Testing Tools
Acunetix Manual Tools is a free suite of penetration testing tools. These tools are not part of the Acunetix product and you need to download an installation package separately. Acunetix Manual Tools include 8 modules: HTTP Editor, Subdomain Scanner, Target Finder, Blind SQL Injector, HTTP Fuzzer, Authentication Tester, Web Services Editor, and HTTP Sniffer. Acunetix Manual Tools are free for private and commercial use but they are not an open-source project. Currently, they are only available for the Microsoft Windows operating system. The tools use a graphical interface only and do not support the command line. Penetration testers can use Acunetix Manual Tools with other tools such as the Metasploit exploitation framework, OWASP Zed Attack Proxy (ZAP), w3af audit framework, Wireshark, etc. to expand their knowledge about a particular security issue detected by an automated web vulnerability scanner or to find advanced security vulnerabilities that automated scanners cannot detect. A combination of automatic and manual tools is the best solution for a web application security testing framework. Automated scanners save a lot of time while manual tools let pen testers explore deeper.
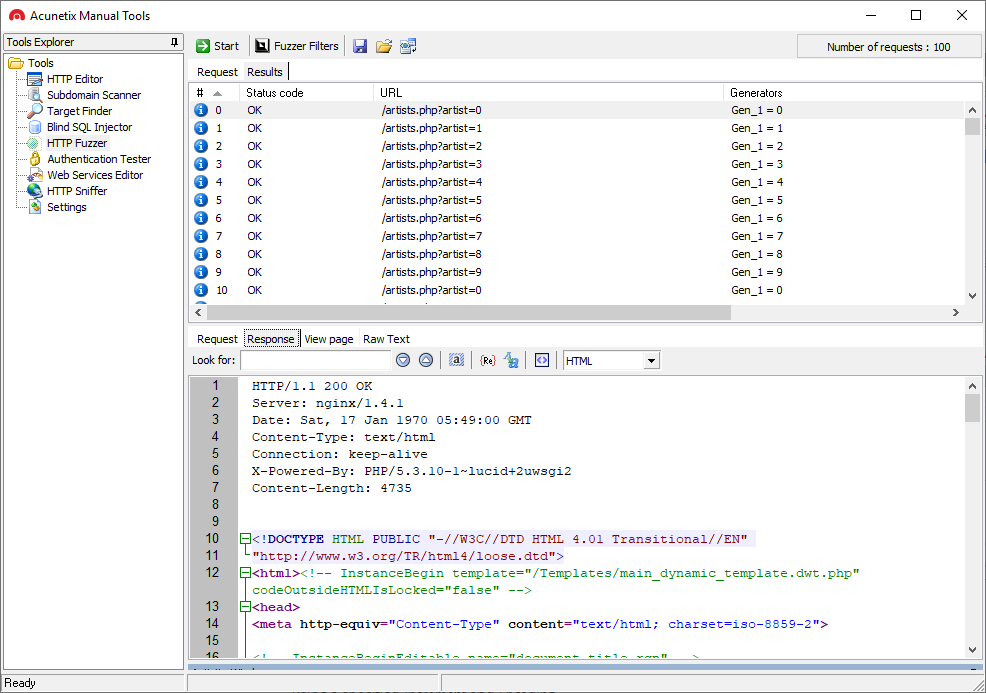
HTTP Security Testing Tools
Several hacking tools in the Acunetix Manual Tools suite focus on HTTP requests and responses:
- The HTTP Editor is one of the most flexible and widely used modules. It lets you create, analyze, and edit client HTTP requests as well as inspect server responses. It also includes an encoding and decoding tool for content and URLs. This tool is useful when analyzing most vulnerabilities including SQL Injections (SQLi) and Cross-site scripting (XSS). To learn how to use this tool, read our article: Getting Started with the Acunetix HTTP Editor.
- The HTTP Sniffer is an intercepting proxy that lets you analyze HTTP requests and responses and manually crawl the site structure. You can also use the HTTP Sniffer to analyze HTTP traffic, trap particular POST or GET requests, and change them manually or automatically to emulate a man-in-the-middle attack. To learn how to use this tool, read our article: Getting Started with the Acunetix HTTP Sniffer.
- The HTTP Fuzzer lets you simulate DoS malware by automatically sending a large number of HTTP requests including invalid, unexpected, and random data to a website. You can use it to test misconfigurations, input validation, and rate-limiting. To learn how to use this tool, read our article: Getting Started with the Acunetix HTTP Fuzzer.

Free Basic Network Security Tools
Some of the modules in the Acunetix Manual Tools cybersecurity suite are network protocol security tools:
- The Target Finder is a port scanner. It lets you run a brute-force port scan to discover web servers running on a given IP address or a range of IP addresses. To learn how to use this tool, read our article: Getting Started with the Acunetix Target Finder.
- The Subdomain Scanner lets you scan a top-level domain to discover subdomains configured in its hierarchy. It uses the target domain DNS server or any other DNS server specified. To learn how to use this tool, read our article: Getting Started with the Acunetix Subdomain Scanner.
While the functionality behind these simple network security tools is easily available in other tool suites such as Kali Linux or network security scanners like nmap, bundling them with more advanced tools helps penetration testers and ethical hackers find web application vulnerabilities faster.

Advanced Web Security Tools
Acunetix Manual Tools security testing software also includes modules for advanced vulnerability assessment:
- The Authentication Tester lets you perform credential security assessment by attempting password cracking. It runs a dictionary attack against HTTP authentication or custom HTML forms. You can use the built-in dictionary or add your own. It is similar to John the Ripper but simpler. To learn how to use this tool, read our article: Getting Started with the Acunetix Authentication Tester.
- The Web Services Editor lets you import a WSDL file to analyze WSDL requests and responses. It has syntax highlighting for all languages so you can easily edit SOAP headers and customize manual attacks. To learn how to use this tool, read our article: Getting Started with the Acunetix Web Services Editor.
- The Blind SQL Injector lets you simulate Blind SQL Injection web application attacks against SQL database servers. Blind SQL Injection vulnerabilities are SQL Injections that do not give a clear response to the attacker. To learn how to use this tool, read our article: Getting Started with the Acunetix Blind SQL Injector.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox