Ethical Hacking Software: Enter Acunetix!
The term “hacking” is typically wrongly associated with malicious intent and security breaches. However, in reality, it is a discipline within which its practitioners wear very different “hats”, some which may come as a surprise to some. Ethical hacking, or white-hat hacking, is a term used to represent individuals who would use the same techniques as a malicious black-hat hacker, however, with the intention to benevolently attack systems on behalf of their owner in order to assess their security before the bad guys do.
Ethical hacking (also commonly referred to as penetration testing) is a field of cybersecurity where security professionals test web applications and network infrastructure for security vulnerabilities. While it requires deep knowledge of how systems work and how to break them, they also need tools to do their job and make their life easier to get results quicker to their customers or other stakeholders. This is where a vulnerability scanner like Acunetix comes into play.
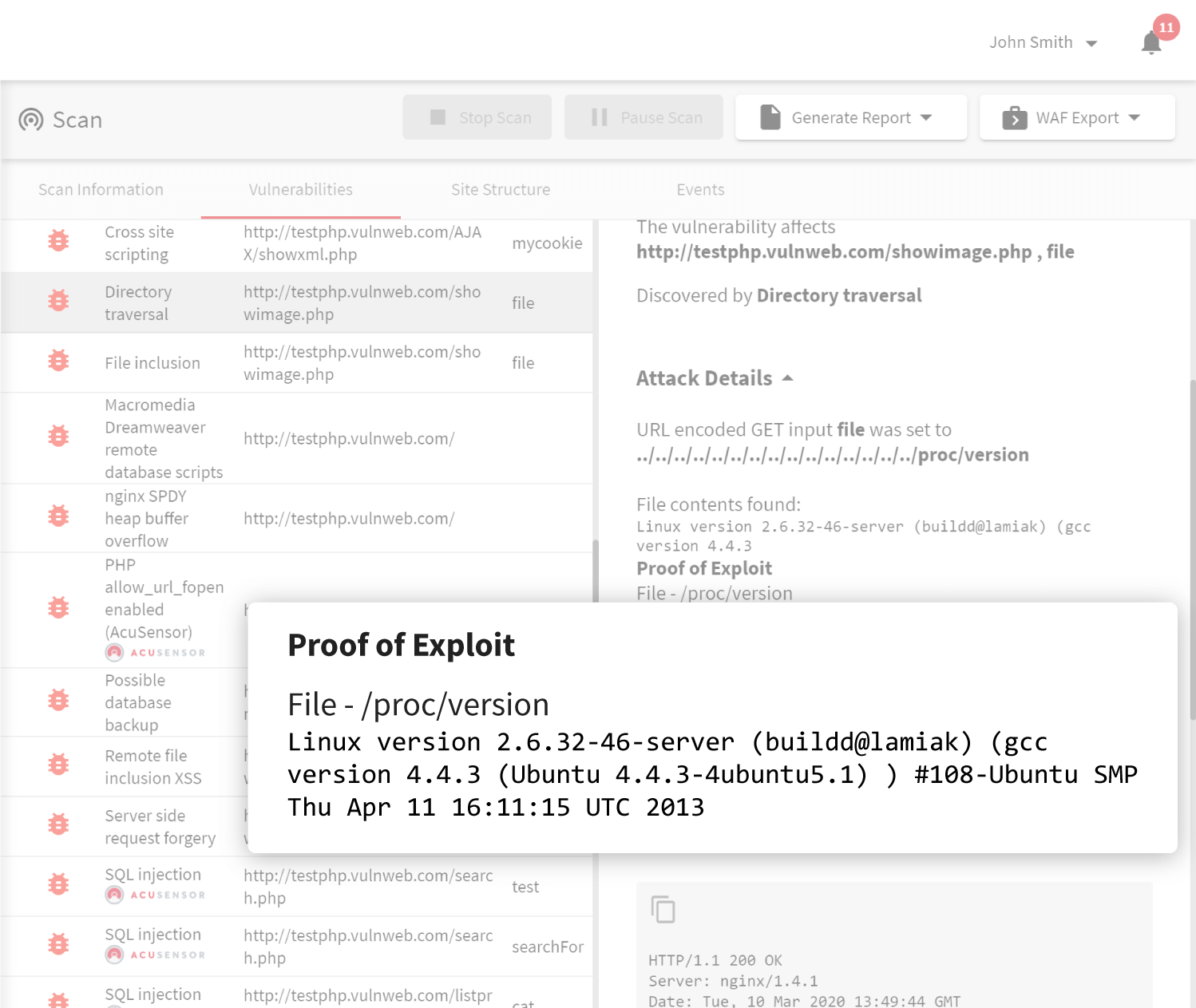
Acunetix is a vulnerability scanner that focuses on automatic security auditing for thousands of web application vulnerabilities at speed and scale. Testing everything from Cross-site Scripting and SQL Injection to web server security, Acunetix provides ethical hackers, developers, and stakeholders alike with the necessary tools and software integrations they need to effectively discover and remediate web application vulnerabilities before the malicious actors have an opportunity to exploit them.
Acunetix achieves this by combining a re-engineered crawler and scanner with a vast array of highly tuned test cases, intelligently designed to run as fast and efficiently as possible.
Unfortunately, while thorough, manual security testing by a penetration tester is time-consuming, expensive, only provides point-in-time security assessment (security tools are not run continuously), and does not provide a scalable approach when organizations have several hundred or even thousands of web applications to test.
Fortunately, automated pen testing software like Acunetix allows organizations to test their web application security quickly, cost-effectively and, most importantly, continuously.
Leave No Stone Unturned with Cutting-Edge Technology Coverage
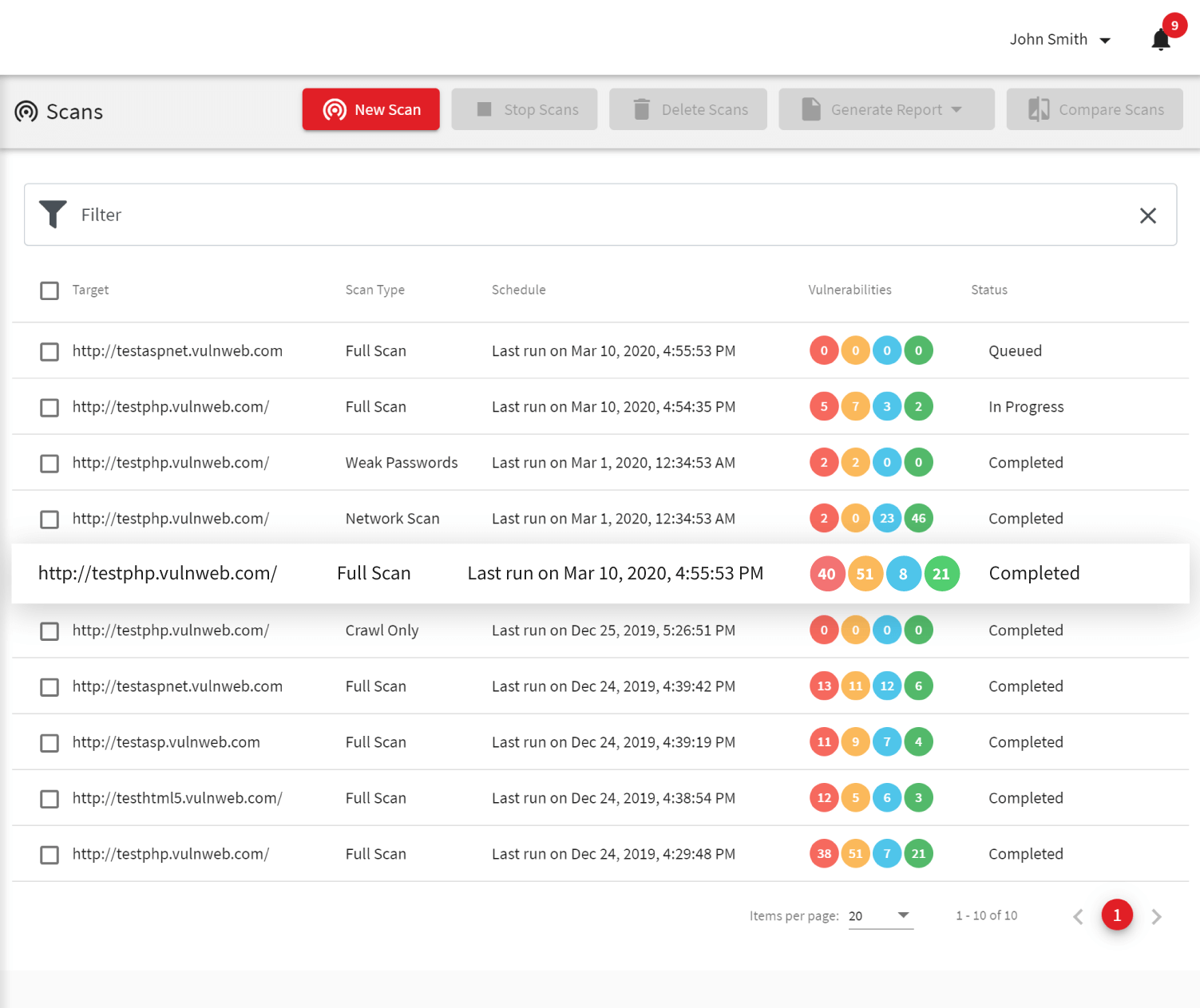
With the Acunetix web vulnerability scanner, security teams can set up scheduled automated scans to test for thousands of web application vulnerabilities and misconfigurations.
While most information security software supports only legacy technologies, Acunetix takes technology support to the next level with the best-of-breed JavaScript support. Unlike most vulnerability scanning software, Acunetix has full support for modern single-page applications (SPAs) and can understand and fully test applications that rely on JavaScript frameworks like React, Angular, Ember, and Vue. This means that Acunetix can scan everything from legacy web applications developed on traditional stacks to modern web apps taking advantage of all the latest and greatest technologies.
Speed and Flexibility Are Not Mutually Exclusive
Unlike many other ethical hacking software, Acunetix is lightning-fast. With a re-engineered core and a highly optimized crawler, every inch of Acunetix is tuned for speed and efficiency, allowing it to scan hundreds of thousands of pages without breaking a sweat.
What’s more, Acunetix can save the progress of a scan midway, pause it, and resume it later on from where it left off entirely automatically. This is crucial for time-boxed ethical hacking tests or when scanning enormous web applications with time restrictions.
Integrations with third-party penetration testing software like PortSwigger Burp Suite make it easy to move between automatic and manual ethical hacking for advanced users who need it. Moreover, findings from Acunetix may be exported to a wide variety of industry-leading web application firewalls (WAFs) such as Imperva SecureSphere, F5 Big-IP ASM, and Citrix WAF.

Easy Reporting and Issue Tracker Integration
It’s no secret that for most ethical hackers reporting is a burden and takes up an enormous amount of time. Acunetix allows you to instantly generate a wide variety of technical, regulatory, and compliance reports such as PCI DSS, HIPAA, OWASP Top 10, and many others.
Additionally, Acunetix allows users to export discovered vulnerabilities to issue trackers such as Atlassian Jira, GitHub, GitLab, Mantis, Bugzilla, and Microsoft Team Foundation Server (TFS), so both ethical hackers and developers working on fixing vulnerabilities can stay perfectly in sync without the need to switch tools or sift through PDFs.
Frequently asked questions
A hacker is a person who is very skilled and who uses their technical knowledge to overcome a problem. A black hat hacker (malicious hacker) is a hacker who has malicious intentions and hacks for criminal purposes. A white hat hacker (ethical hacker) is a hacker who hacks to help secure systems. A grey hat hacker is a white hat hacker who sometimes violates laws or ethical standards but does not have bad intentions.
Ethical hacking means trying to find a vulnerability in a system to show the creators of this system how to fix it. Ethical hacking is often called penetration testing. When automated, it is called vulnerability scanning.
Read more about how penetration testing and vulnerability scanning go together.
Ethical hacking is legal if the owner of the target computer system knows about it or openly welcomes it. For example, it is legal if you are hired by a company to hack their systems. It is also legal if a company publishes a hacking bounty program. Also, note that this may be different in different countries.
Read more about how ethical hackers from Russia legally hack Google.
Professional ethical hackers first use vulnerability scanners to automate their work. Then, they perform additional manual analysis using manual penetration testing tools. Such tools include exploit frameworks, listening proxies, and other investigative software.
