Recently a new high risk vulnerability was discovered in the highly popular TimThumb script. TimThumb is a “A small php script for cropping, zooming and resizing web images (jpg, png, gif). Perfect for use on blogs and other applications.“
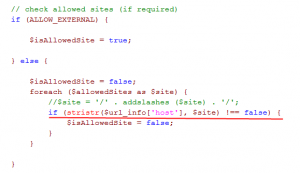
TimThumb is included in a lot of WordPress plugins and themes (free and paid). Exploiting this vulnerability an attacker can upload and excute a PHP file of his choice on a vulnerable website. Here is the vulnerable code.
By default the script allows uploding files from a list of trusted external domains specified below:
// external domains that are allowed to be displayed on your website $allowedSites = array ( 'flickr.com', 'picasa.com', 'blogger.com', 'wordpress.com', 'img.youtube.com', );
It should not be possible to upload files from another external domain. However, the check is flawed because you can bypass it using a domain like blogger.com.hacker.com. This domain passes the check but belongs to hacker.com, making the script exploitable.
Hackers are already exploiting this vulnerability in the wild (for example we’ve seen instances of this script being used in exploits : hxxp://blogger.com.zoha.vn/db/load.php)
If you are vulnerable you should contact the author of the affected plugin/theme and ask them to provide you with a fixed version. If that fails, you can download the fixed version (v1.34) from the TimThumb project page (http://code.google.com/p/timthumb/).
We’ve researched this issue and compiled a list of plugins and themes that are affected by this vulnerability.
The list of WordPress plugins that include a vulnerable version of TimThumb (pre TimThumb version 1.34).
- portfolio-slideshow-pro
- wp-mobile-detector
- a-wp-mobile-detector
- igit-related-posts-with-thumb-images-after-posts
- dukapress
- verve-meta-boxes
- db-toolkit
- logo-management
- wp-marketplace
- islidex
- aio-shortcodes
- category-grid-view-gallery
- WPFanPro
- igit-posts-slider-widget
- wordpress-gallery-plugin
- cms-pack
- Premium_Gallery_Manager
- dp-thumbnail
- placid-slider
- nivo-slider
- photoria
- LaunchPressTheme
- kc-related-posts-by-category
- journalcrunch
- download-manager
- wordpress-thumbnail-slider
- sugar-slider
- optimizepress
And here is a list of WordPress themes that are affected by this vulnerability because they include this script.
- Minimo
- Polished
- Minimal
- nebula
- TheCorporation
- TheStyle
- TuaranBlog
- striking
- MyCuisine
- AskIt
- Webly
- Aggregate
- TheSource
- reviewit
- kelontongfree
- Mentor
- SimplePress
- journalcrunch
- ecobiz
- Magnificent
- timthumb.php
- Olympia
- kingsize
- Chameleon
- DelicateNews
- videozoom-v2.0-original
- videozoom
- Envisioned
- twicet
- u-design
- genoa
- OptimizePress
- Modest
- mocell
- ephoto
- Theme
- InReview
- lightpress
- hostme
- PersonalPress
- Cadca
- arras
- tiwinoo_v3
- MyProduct
- sc4
- InterPhaseTheme
- InStyle
- LightBright
- TheProfessional
- mnfst
- freshnews
- ArtSee
- Boutique
- eStore
- Avenue
- twentyten
- XSWordPressTheme
- adcents
- Nova
- MyPhoto
- eGallery
- Striking_Premium_Corporate
- default
- Lycus
- manifesto
- cold
- DynamiX
- tarnished
- Nyke
- linepress
- DJ
- adria
- zimex
- peano
- ElegantEstate
- delight
- kelontong-free
- duotive-three
- SobhanSoft_Theme
- PureType
- yamidoo_pro
- vulcan2.1
- eGamer
- Wooden
- peritacion
- AmphionPro
- trinity
- dandelion_v2.6.3
- Juggernautgrande
- juggernaut-theme
- BlackLabel_v1.1.2
- Feather
- reviewit1
- zinepress_v1.0.1
- tribune
- photoria
- vilisya
- DailyNotes
- Basic
- minerva
- anthology_v1.4.2
- ModestTheme
- purevision
- parquet
- framed-redux
- eceramica
- InterPhase
- epsilon
- Striking
- thedawn
- peava
- Newspro
- telegraph
- averin
- telegraph_v1.1
- Memoir
- NewsPro
- CircloSquero
- vassal
- maxell
- 13Floor
- wpanniversary
- OnTheGo
- Glider
- mohannad-najjar222
- mohannad-najjar2
- arthemia
- tuufy7
- photoframe
- beach-holiday
- blacklabel
- cadabrapress
- snapwire
- bizpress
- themesbangkoofree
- TOA
- D4
- eNews
- vulcan
- overtime
- rockwell_v1.0
- vicon
- wideo
- CherryTruffle
- mio
- rttheme13
- Linepress
- DeepFocus
- advanced-newspaper202
- OptimusPrime
- Quadro
- Lumin
- minima
- identity
- U-design.v1.1.2_hkz
- KP
- Petra
- services
- 13FloorTheme.php
- BD
- PolishedTheme
- 13FloorTheme
- kiwinho
- graphix
- jerestate
- centro
- corage
- Reporter
- TheTravelTheme
- XSBasico
- openhouse
- seosurfing1
- bluebaboon
- Newspro-2.8.6
- nd
- zoralime
- GrupoProbeta
- eBusiness
- purplex
- kitten-in-pink
- FashionHouse
- WhosWho
- Deviant
- Bold
- BusinessCard
- EarthlyTouch
- GrungeMag
- LightSource
- Simplism
- TidalForce
- Glow
- Influx
- StudioBlue
- jpmegaph
- redina
- tritone
- dandelion_v2.5
- Bluesky
- ColdStone
- silveroak
- newspro
- GamesAwe
- caratinga.net
- SimplePressTheme
- MyResume
- MyApp
- theme
- bigcity
- dandelion_v2.6.1
- chronicle
- cuizine
- thesis_18
- advanced-newspaper_new
- Event
- wpbedouine
- rt_affinity_wp
- arry12
- backup-TheStyle
- ExploreFeed
- zzzzzzzzz
- Bluemist
- Hermes
- cleartype_v1.0
- polariswp
- Chameleon 1.6
- sniper
- adena
- ariela
- FreshAndClean
- wp-creativix
We are pretty sure these lists are not complete, it’s very probable that other themes and plugins are affected.Because there are so many plugins and themes vulnerable, we expect a high number of people to be affected by this vulnerability. Please check your site/blog security and spread the word around.
Get the latest content on web security
in your inbox each week.