In a bid to ensure WordPress Security, an Acunetix web vulnerability scan is able to detect a WordPress installation, and will execute various WordPress related checks when the popular blogging web application is identified. When WordPress is detected, Acunetix will issue the following knowledge base entry.
Acunetix will also scan WordPress for various security vulnerabilities which can lie in WordPress itself, WordPress themes and plugins, or result from misconfigurations. I will detail these security checks in the rest of this article.
All the checks listed below are available in both Acunetix On-Premises and Acunetix Online.
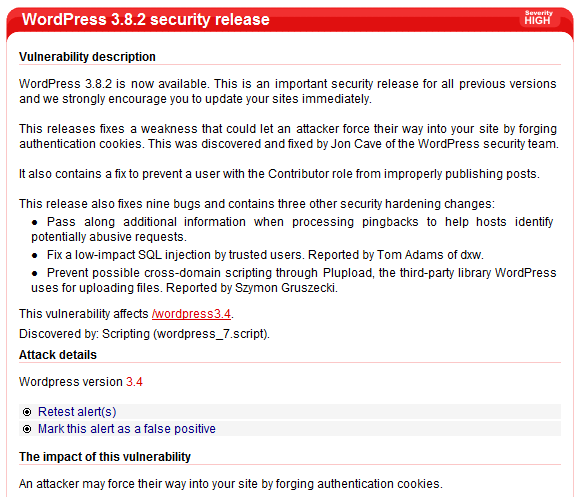
Check for vulnerable WordPress versions
Acunetix checks if the WordPress version you are running has any known security vulnerabilities. A high security alert, similar to the one shown in the screenshot will be raised when a vulnerable WordPress version is detected. The attack details will show the version that has been detected.
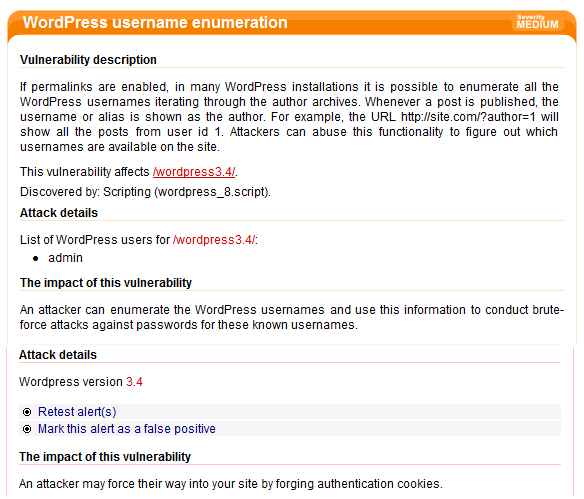
WordPress Username Enumeration
Acunetix uses various techniques to enumerate WordPress users. The possibility to enumerate users gives a head start to someone trying to hack your WordPress installation, since the attacker would be able to run a dictionary attack against the password of the users that have been identified.
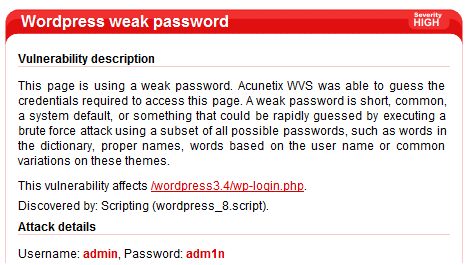
Identify users with weak passwords
For the users that Acunetix identifies during the scan, it will try to detect if they are using weak passwords. Apart from using a small password list with the most common passwords, Acunetix will also try using different combinations of the username, including using leetspeak.
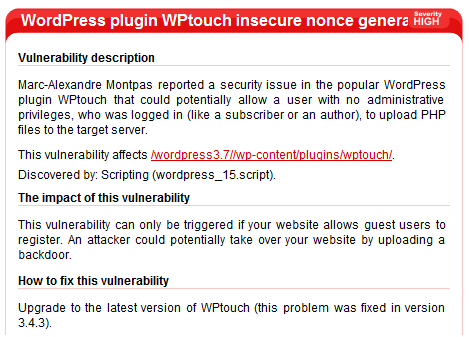
Highlight vulnerable plugins / themes
Acunetix is also able to detect plugins that are installed in WordPress that are known to contain security vulnerabilities. Unfortunately, such issues might exist even in well-known plugins, such as WPtouch shown in the screenshot. Acunetix will flag such plugins. Generally upgrading to the latest version of the plugin would solve the problem, however in some rare cases, the plugin would need to be disabled or removed.
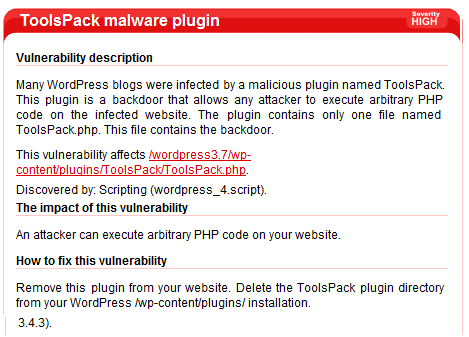
Identify malicious plugins / themes
WordPress too has its share of malware, which generally disguises itself either as a plugin or as a theme. The description of such malware tries to lure WordPress users into installing the malicious plugin or theme.
The screenshot shows an example of a malicious plugin called ToolsPack. Although it promised to “Supercharge your WordPress site with powerful features previously only available to WordPress.com users”, the only functionality that it provides is a backdoor allowing the attacker to execute arbitrary PHP code on the infected website.
List installed WordPress plugins
Acunetix is able to detect and provide information on the 1000 most popular WordPress plugins. The WordPress plugins that are detected are listed in the WordPress plugins Knowledge Base. Acunetix also provides a short description for each plugin, and shows the version number that has been detected, together with the latest version of the plugin, allowing you to easily detect plugins that need to be updated.
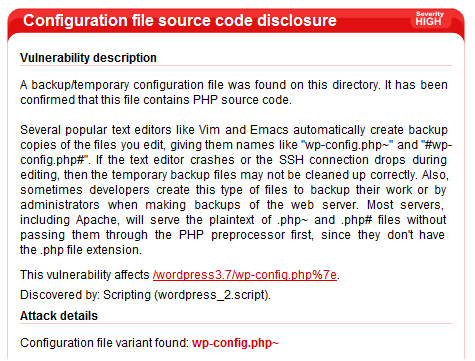
WordPress Configuration File Disclosure
Although most of the common configuration settings are available through the WordPress admin interface, the wp-config.php file holds crucial settings that WordPress depends on to operate. Amongst other settings, the wp-config.php file contains settings such as database connection information as well as unique keys and salts that WordPress uses for authentication.
Changes to wp-config.php are usually done by first creating a backup of the known working configuration, before proceeding with manually altering the file in a text editor. Sometimes, an administrator may rename the file in such a way where the *.php extension is modified, and some text editors create backups when a file is edited (for instance wp-config.php~). This means that the backed up file containing sensitive information suddenly becomes available to whoever is able to guess the name of the backup file since the file’s extension is no longer that of *.php, which as a result would simply download the file for the user requesting it (as opposed to executing the PHP file on the server). It is also worth noting that some text editors such as Vim and Emacs automatically create backup files similar to the ones described above, effectively resulting in the same vulnerability.
Acunetix flags this as a high alert, since this file contains sensitive configuration settings, such as the location, username and password of the WordPress database, and thus should not be available to anonymous users.
Get the latest content on web security
in your inbox each week.