Recently somebody posted on Reddit about a WordPress scanner that is taking advantage of a new WordPress vulnerability. The vulnerability is abusing the Pingback system, which is a well-known feature that’s used by a lot of bloggers.
What is a Pingback?
Quoting Wikipedia: A pingback is one of three types of linkbacks, methods for Web authors to request notification when somebody links to one of their documents. This enables authors to keep track of who is linking to, or referring to their articles. Some weblog software, such as Movable Type, Serendipity, WordPress, and Telligent Community, support automatic pingbacks where all the links in a published article can be pinged when the article is published.
WordPress has an XMLRPC API that can be accessed through the xmlrpc.php file. One of the methods exposed through this API is the pingback.ping method. With this method, other blogs can announce pingbacks. When WordPress is processing pingbacks, it’s trying to resolve the source URL, and if successful, will make a request to that URL and inspect the response for a link to a certain WordPress blog post. If it finds such a link, it will post a comment on this blog post announcing that somebody mentioned this blog post in their blog.
This can be abused in at least fours ways:
- WordPress is trying to resolve the Source URL and will return different error messages if the Source URL exists (host exists) or not. This can be abused by attackers to try to guess hosts inside the internal network. The attackers can use URLs like http://subversion/ or http://bugzilla/or http://dev/to see if these hosts exist in the internal network.
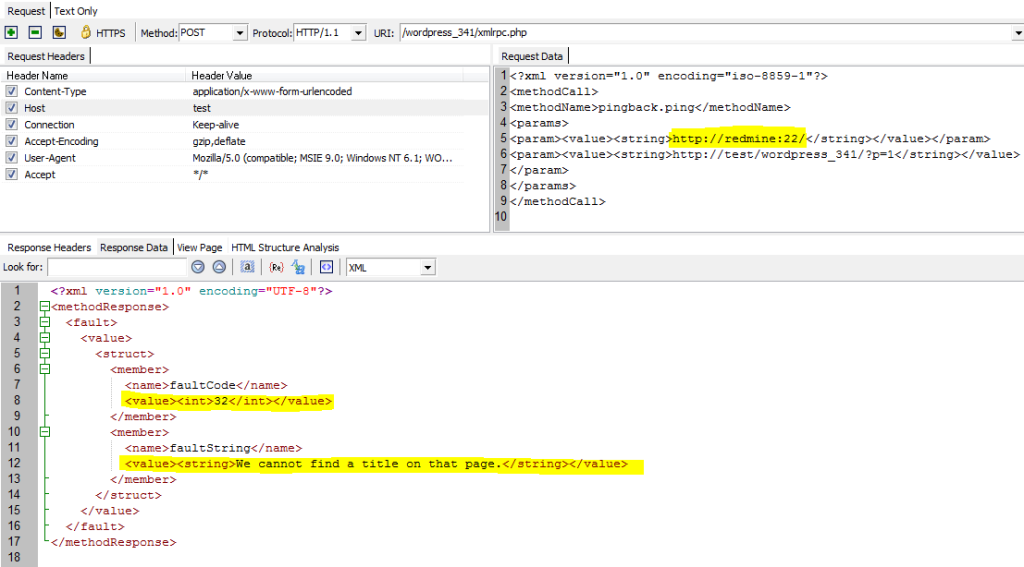
- If the Source URL is resolved, WordPress will try to connect to the port specified in the URL. Therefore, if an attacker will use a URL like http://subversion:22/, WordPress will try to connect to the host subversion on port 22. The responses are different if the port is open or closed. Therefore, this functionality can be used to port scan hosts inside the internal network.
- This can also be used for distributed DOS (Denial of Service) attacks. An attacker can contact a large number of blogs and ask them to pingback a target URL. All of these blogs will attack the target URL.
- From the tests I’ve carried out, I’ve seen that WordPress is also supporting URLs with credentials. So, an attacker can use a URL like http://admin:admin@192.168.0.1/changeDNS.asp?newDNS=aaaa to reconfigure the internal router like in the email hack attack.
I’ve made some screenshots to demonstrate how WordPress is returning different error messages for valid and invalid hosts/ports.
Invalid Host

Valid Host
I’ve implemented an Acunetix WVS script to test this vulnerability. This script will try to resolve various common internal hosts and try to connect to common ports. In the end, it will report the successful attempts. The script is available in the latest build (20121213) of Acunetix WVS. A sample alert looks like this:

How do you protect against this vulnerability? Currently there is no fix. Disabling pingbacks and trackbacks from the Discussion Settings page doesn’t fix the problem either. The issue was reported to the WordPress Team and will probably be fixed soon. Until then, you can rename/delete the xmlrpc.php file. Please let me know if you have a better workaround.
** Note: The issue described in this article has been addressed in WordPress 3.5.1.
Get the latest content on web security
in your inbox each week.



