Cisco have just published their 2016 Annual Security Report, which covers the last year in cyber security while also looking ahead to growing threats.
Particularly interesting is the Threat Intelligence section, which examines some of the most common exploits, malware kits and targeted industries in 2015. Naturally Adobe Flash is quite a prominent feature in this section; the sheer number of vulnerabilities discovered in 2015 has had two consequences, firstly the use of Flash is declining but unfortunately this doesn’t happen as quickly as the speed at which attackers can take advantage. The second consequence of all these vulnerabilities is that they are being widely incorporated in malware kits and are the most common publicly available exploits for attackers.
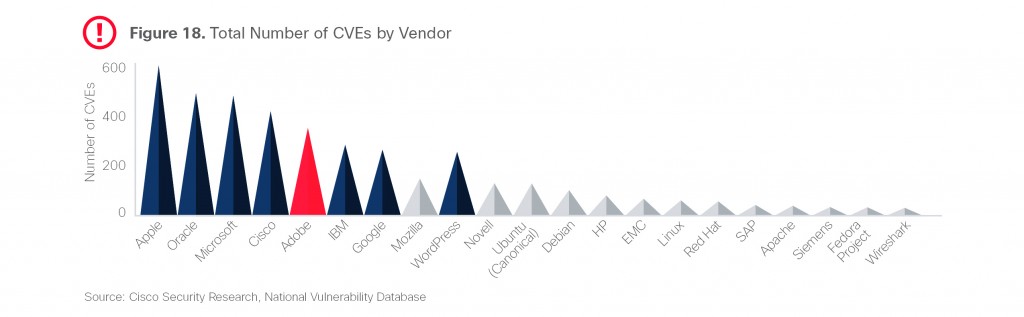
As you can see from the figure above Adobe definitely ranks highly among the main vendors for its level of vulnerabilities and WordPress isn’t far behind. While having had 24 vulnerabilities in the WordPress product itself, it suffered an additional 240 vulnerabilities through plugins and themes. A small section further in the report also examines the use of WordPress by attackers, noting a 220% rise in 2015, of WordPress domain servers being hijacked for use in attacks.
Where Adobe does rank most highly is in the number of public exploits available, placing above even the big OS companies Microsoft and Apple. This makes sense, as while operating system updates are rolled out regularly, patching of products such as Adobe are up to the user, meaning millions of users remain exposed even months after a vulnerability has been discovered. A zero-day can give attack potential for many months, or even years to follow.

Another area the report examines is the volume of attack traffic received by the various different industries, a total of 28. The most commonly targeted include government, electronics companies, healthcare and professional services, who all experienced a peak of high volume attack traffic at some point during the time studied. These four sectors were described as being targeted with Trojan-related attacks, while the government targets also faced a large volume of PHP injection attacks.

Finally in their Threat Intelligence chapter, the malware-based block activity was broken down by country, giving a geographical picture of where most attacks were directed. Unlike geographical breakdowns which we might see in other reports, the stand out target here was Hong Kong, who received a huge increase in malicious traffic. The numbers represent the net change in the last twelve months and as we can see Hong Kong have had 9 times the increase of the USA, which is usually one of the main geographical targets. The report authors have put this down to the presence of ‘large, commercially viable networks’ however it did fluctuate throughout the year.
Another chapter of the report is dubbed ‘Industry Insights’ and examines a small variety of escalating issues such as the challenges of encryption, increased criminal activity on WordPress, aging infrastructure and the weakness of SMBs. A small but encouraging section describes the growing commitment to managing vulnerabilities, both from the major providers increase in updates and their communications about such updates but also through the increase in ‘cumulative alert totals’. Cumulative alerts are designed to give notice of open-source and proprietary product updates to allow users to keep on top of any possible vulnerabilities. The use of these rose 21% between 2014 and 2015.
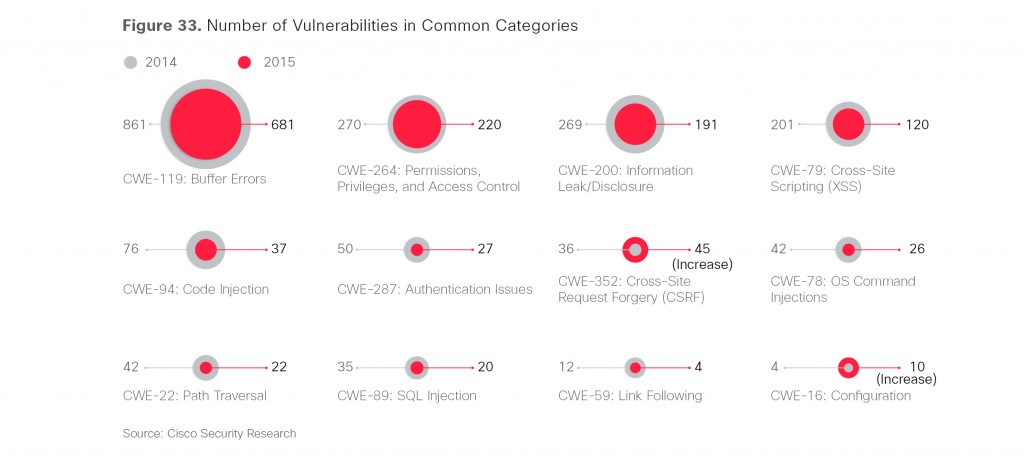
The most interesting section of this report might be the small section devoted to Threat Categories, where the levels of different types of vulnerabilities are compared to the previous year. Overall, the the number of the main vulnerabilities decreased; in the case of Cross-Site Scripting by a whopping 47%. Information disclosure vulnerabilities also dropped 15% and SQL Injection also declined. The only two where an increase was noted was Cross Site Request Forgery, where 36 vulnerabilities increased to 45 in 2015 and Configuration vulnerabilities, which more than doubled from 4 to 10.
Get the latest content on web security
in your inbox each week.




