Yesterday, the details of the latest vulnerability affecting SSL started emerging, and in no time, everyone started talking, or rather blogging about POODLE. POODLE stands for Padding Oracle On Downgraded Legacy Encryption and affects the 15 year old SSLv3, which should have been deprecated and abolished soon after the subsequent version of SSL/TLS was made available.
However, support for legacy systems prevailed, and here we stand today with over 98% of web sites and the major web clients still providing support for SSLv3 and thus vulnerable to information leaks through POODLE.
You might be thinking that you and your web site users are safe, since you are using the latest version of your web server, which supports the latest version of TLS. Unfortunately, you are still affected, since SSL /TLS implementations will fall back to previous versions of the SSL/TLS protocol when a connection with the latest version of SSL/TLS cannot be completed. The man-in-the-middle can easily drop the connection to the server in order to exploit the SSL protocol downgrade dance and cause the SSL/TLS communication to occur using SSLv3.
Once that is done, the attacker can use POODLE to steal the “encrypted” data, such as the HTTP cookies, giving the SSL session invader access to encrypted data and restricted areas. This is achieved by performing multiple requests in order to identify the contents of each byte in the encrypted data. Doing this over and over again allows the attacker to determine the unencrypted content of what was supposed to be encrypted.
The best way to protect against this vulnerability is to disable the usage of older versions of SSL/TLS in both web server and web browsers. If disabling SSLv3 is not possible, such as if the web site needs to provide support for Internet Explorer v6, then the web server should implement support for TLS_FALLBACK_SCSV mechanism, which will use older versions of SSL/TLS only when it is really necessary, disallowing the protocol downgrading when it is not required.
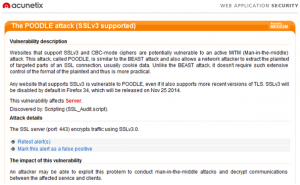
Acunetix has been updated to identify servers that still provide support for SSLv3
If you are using Acunetix Web Vulnerability Scanner, you can install the update from General > Program Updates > Click on Download and Install updates. Scan your web servers to identify the ones which are vulnerable to POODLE.
Acunetix Online Vulnerability Scanner has been updated so that your next scan will check for POODLE.
External References:
- This POODLE bites: exploiting the SSL 3.0 fallback
- The POODLE Attack and the End of SSL 3.0
- This POODLE bites: exploiting the SSL 3.0 fallback (technical paper)
- How POODLE Happened
Get the latest content on web security
in your inbox each week.