In a man-in-the-middle attack (MITM), a black hat hacker takes a position between two victims who are communicating with one another. In this spot, the attacker relays all communication, can listen to it, and even modify it.

Imagine that Alice and Barbara talk to one another on the phone in Lojban, which is an obscure language. Nancy is a secret agent who needs to listen in on their conversation but who cannot tap the phone line. Nancy is very clever and talented, so she does the following:
- Nancy observes Alice and Barbara for a while. She notices that Alice always calls Barbara, not the other way around.
- Nancy recognizes that Alice and Barbara are speaking in Lojban. She learns that language.
- Nancy slips a business card into Alice’s purse. The card says “Barbara” but it has Nancy’s phone number.
- When Alice calls this number, it is Nancy who receives the call. She answers in Lojban and imitates Barbara’s voice.
- Nancy immediately calls Barbara on another phone. She imitates Alice’s voice, saying hello in Lojban.
- Nancy continues both conversations switching between them as needed.
Now Alice and Barbara are both certain that they are talking to one another. In reality, they are talking to Nancy who relays communication between them. Nancy knows all the secrets. She may also manipulate the information that Alice and Barbara are sharing with one another.
To pull this off, Nancy uses several tools. For example, she spoofs Barbara’s phone number, she figures out the encryption (Lojban language), and she authenticates by imitating voices. Black hat hackers do very similar things in the IT world.
Are Man-in-the-Middle Attacks Dangerous?
In the world of IT security, black hat hackers usually use man-in-the-middle attacks to eavesdrop on communications between a client and a server. This includes HTTPS connections to websites, other SSL/TLS connections, Wi-Fi connections, and more.
Such hackers have two primary goals: to gain access to sensitive information and/or to manipulate transmitted content. In practice, they can use MITM attacks:
- To get personal information for identity theft
- To get login credentials, for example, to gain access to an online bank account
- To change the target account number to their own when the user is making a bank transfer
- To get a credit card number when the user is paying at an online shop
You must also remember that websites are not the only target of MITM attacks. A very common target are emails which by default do not use any kind of encryption. If an attacker can get access to an email account, they may intercept and spoof emails.
Real-Life Examples of MITM Attacks
Man-in-the-middle attacks were known a long time before the advent of computers.
- One of the oldest cases was the Babington Plot. Communications between Mary Stuart and her fellow conspirators was intercepted, decoded, and modified by a cryptography expert Thomas Phelippes.
- During World War II, British intelligence conducted MITM attacks against Nazi forces using Aspidistra devices. Cracking of the Enigma code could also be considered a MITM attack.
In the world of computing, some of the most famous cases linked to MITM attacks were the following:
- In 2013, information was leaked about the Quantum/FoxAcid MITM system employed by NSA to intercept TOR connections.
- In 2014, Lenovo installed MITM (SSL Hijacking) adware called Superfish on their Windows PCs.
- In 2015, a British couple (the Luptons) lost £340,000 in an email eavesdropping / email hijacking MITM attack.
How Do Man-in-the-Middle Attacks Work?
A black hat hacker may attack a connection that is secure (encrypted) or not. In both cases, the first goal is to intercept the connection – like Nancy first has to slip a business card into Alice’s purse. There are many ways to do this including ARP spoofing, IP spoofing, and DNS spoofing. The attacker may also use other attack vectors to take control of the victim’s machine or the server and eavesdrop from there.
ARP Spoofing (ARP Cache Poisoning)
ARP (Address Resolution Protocol) translates between the physical address of an Internet device (MAC address – media access control) and the IP address assigned to it on the local area network. An attacker who uses ARP spoofing tries to inject false information onto the local area network to redirect connections to their device.
For example, your router has the IP address 192.168.0.1. To connect to the internet, your laptop needs to send IP (Internet Protocol) packets to this address. First, it must know which physical device has this address. The router has the following MAC address: 00-00-00-00-00-01.
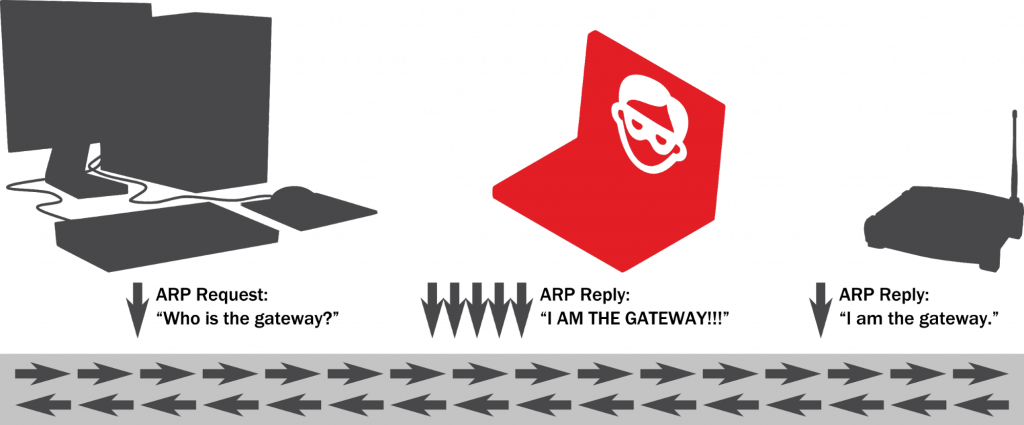
Let’s say that Nancy is no longer working with phones but she is a black hat hacker:
- Nancy injects false ARP packets into the network.
- These ARP packets say that the address 192.168.0.1 belongs to Nancy’s device with the following MAC address: 00-00-00-00-00-2A.
- The ARP cache stores false information associating IP 192.168.0.1 with MAC 00-00-00-00-00-2A.
- The next time your laptop is trying to connect to the internet, it connects to Nancy’s machine.
- Nancy’s machine connects to the router (00-00-00-00-00-01) and connects you to the internet, so you don’t even know that Nancy is there.
IP Spoofing (IP Address Spoofing)
IP spoofing means that a computer is pretending to have a different IP address – usually the same address as another machine. On its own, IP spoofing is not enough for a MITM attack. However, an attacker may combine it with TCP sequence prediction.
Most internet connections are established using TCP/IP (Transmission Control Protocol / Internet Protocol). When two devices on the network connect to one another using TCP/IP, they need to establish a session. They do it using a three-way handshake. During this process, they exchange information called sequence numbers. The sequence numbers are needed for the recipient to recognize further packets. Thanks to sequence numbers, the devices know the order in which they should put the received packets together.
In this situation, the attacker first sniffs the connection (listens in). This is very easy on a local network because all IP packets go into the network and may be read by any other device. The attacker learns the sequence numbers, predicts the next one, and sends a packet pretending to be the original sender. If that packet reaches the destination first, the attacker intercepts the connection.
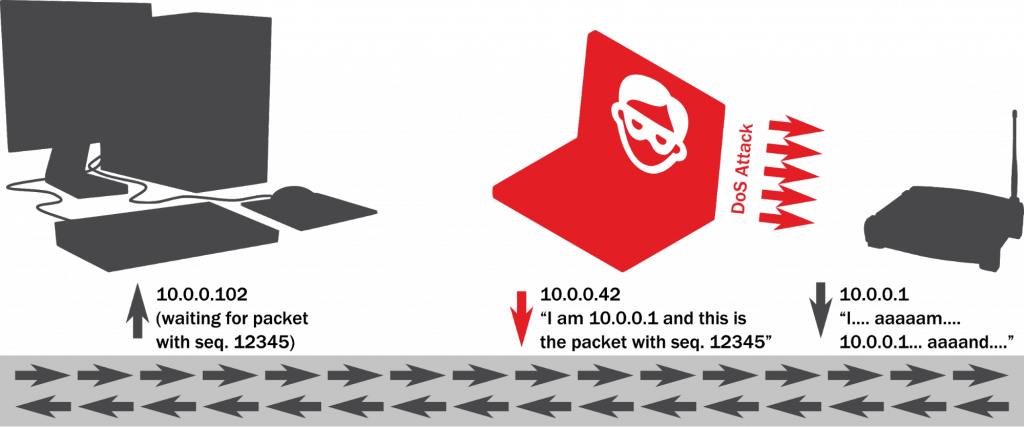
Let’s go back to Nancy who wants to try IP spoofing with TCP sequence prediction this time:
- Nancy joins your local network as 10.0.0.42 with her laptop and runs a sniffer. The sniffer software lets her see all the IP packets that go through the network.
- Nancy wants to intercept your connection to the gateway (10.0.0.1). She looks for packets between you (10.0.0.102) and the gateway and then predicts the sequence number.
- At the right moment, Nancy sends a packet from her laptop. The packet has the source address of the gateway (10.0.0.1) and the correct sequence number, so your laptop is fooled.
- At the same time, Nancy floods the real gateway with a DoS attack. The gateway works slower or stops working for a moment. Nancy’s packet reaches you before the packet from the gateway does.
- Nancy convinced your laptop that her laptop is the gateway. Now she convinces the gateway that her laptop is 10.0.0.102 (you), and the MITM attack is complete.
DNS Spoofing (DNS Cache Poisoning)
ARP spoofing and IP spoofing need the attacker to connect to the local network segment that you use. An attacker using DNS spoofing can be anywhere. It’s more difficult because your DNS cache must be vulnerable. However, if successful, it can affect a large number of victims.
DNS (Domain Name System) is the system used to translate between IP addresses and symbolic names like www.example.com. This system has two primary elements: nameservers (DNS servers) and resolvers (DNS caches). The nameserver is the source of authoritative information. Usually, there are two or three systems that keep that information for every domain. For example, the IP number for www.example.com is stored on two nameservers: sns.dns.icann.org and noc.dns.icann.org. You can check this using the Google DNS lookup tool.
If every client that wants to connect to www.example.com connected to these two servers every time, they would be overloaded. That is why every client uses its local resolver to cache information. If the cache does not have information on www.example.com, it contacts sns.dns.icann.org and noc.dns.icann.org to get 93.184.216.34. Then, it stores the IP address locally for some time. All the clients that use this resolver get the address from the cache.
A DNS spoofing attack is performed by injecting a fake entry into the local cache. If a black hat hacker does that, all clients connected to this cache get the wrong IP address and connect to the attacker instead. This lets the attacker become a man-in-the-middle.

This time, Nancy cannot connect to your network so she tries DNS spoofing:
- Nancy knows, that you use 203.0.113.255 as your resolver (DNS cache).
- Nancy also knows that this resolver is vulnerable to poisoning (uses BIND 4 software).
- Nancy poisons BIND 4 at 203.0.113.255 and stores information that www.example.com is 198.51.100.123.
- When you type www.example.com in your browser, the site that you see is Nancy’s site.
- Nancy connects to the original site to complete the attack.
Other Methods Used to Intercept Connections
Black hat hackers may use many more methods to place themselves between the client and the server. These methods usually belong to one of the following three categories:
- Server compromise: An attacker may use another technique to gain control over the server that you connect to. They can then place their own software on that server to intercept connections with you. For example, they may start with SQL Injection and escalate to full system compromise, then place MITM software on the compromised web server. They might also abuse a code injection vulnerability to place a shell on the server.
- Client compromise: An attacker may place a rogue application such as a trojan on your machine (for example, man-in-the-browser). The application can listen in on all your connections and allow for MITM attacks. To do this, the attacker may get you to click a malicious link or may use another technique to have you download malware. They might, for example, perform a Cross-site Scripting attack on your favorite web application and place malicious JavaScript.
- Communications compromise: An attacker may take over a machine that routes information between the client and the server. For example, a network router with vulnerable software or a public Wi-Fi hotspot. Black hat hackers may also place their own malicious Wi-Fi access point in your vicinity so that you connect to it. If your Wi-Fi network connection uses a vulnerable encryption protocol like WEP, you may be a target of Wi-Fi eavesdropping.
How Do Attackers Listen In?
If the victim uses a secure connection, being in the middle is not enough. Nancy must understand the language that Alice and Barbara are using (Lojban). She must also be able to speak it fluently and imitate Alice’s and Barbara’s voices. This is needed so that Alice and Barbara are still sure that they are talking to one another. Some of the techniques used for this in the IT world are HTTPS spoofing, SSL hijacking, and SSL stripping.
HTTPS Spoofing (IDN Homograph Attacks)
International domain names (IDNs) can contain Unicode characters. Some Unicode characters look similar to ASCII characters. Black hat hackers use this to fool victims. A victim visits a fake website controlled by the attacker who intercepts information and relays it to the real website.
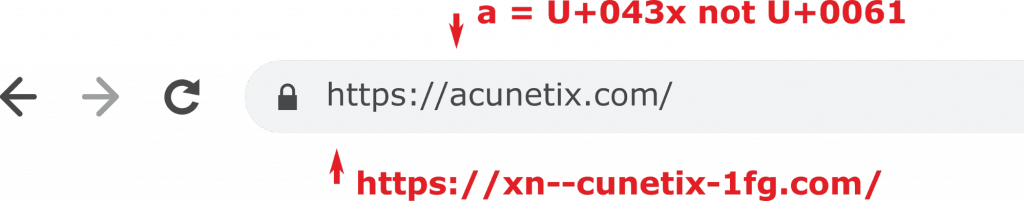
For example, Nancy wants you to visit a fake Acunetix website аcunetix.com (the Cyrillic а looks exactly like the ASCII a):
- Nancy uses Punycode to register the domain аcunetix.com:
xn--cunetix-1fg.com(you can try to create your own using Punycoder). - Nancy buys a legitimate SSL/TLS certificate for аcunetix.com.
- Nancy sends you a malicious link to visit the fake Acunetix site.
- When you visit the site, you can see https and a lock symbol in the address bar so you are not alarmed.
- In the background, Nancy relays all the information sent by you to the real Acunetix site.
Current browsers (Chrome, Firefox, Opera, Internet Explorer, Edge, Safari) have protection against HTTPS spoofing (IDN homograph attacks). For example, they display Punycode in the address bar instead of national characters. However, websites and emails may still contain links in Unicode that look exactly like originals.
SSL Hijacking
Anyone can generate an SSL/TLS certificate for any domain. An attacker who intercepts a connection can generate certificates for all domains that the victim visits. They can present these certificates to the victim, establish a connection with the original server, and relay the traffic. This is called SSL hijacking.
However, your browser trusts only certificates that are signed by a trusted Certificate Authority (CA). If the certificate is not signed by a trusted CA, browsers display clear warnings or even refuse to open a page. Therefore, an attacker needs a way to make your browser believe that the certificate can be trusted. To do it, they must add their CA to the trusted certificate store on your computer. This can be done using other attack vectors.
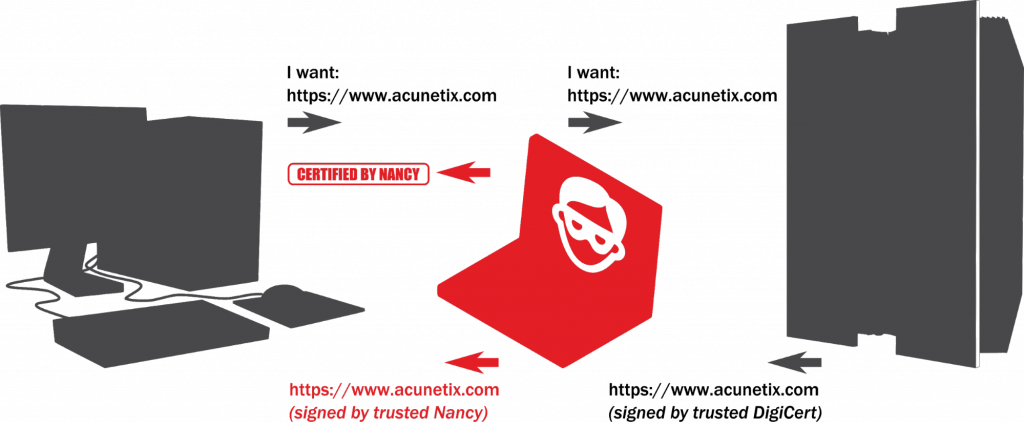
If Nancy wants to listen in on your SSL/TLS connections using SSL hijacking, this is what she does:
- Nancy gets you to download and install her CA certificate using some other type of attack.
- Every time you visit a secure site, for example, acunetix.com, Nancy intercepts the connection.
- Nancy generates a certificate for acunetix.com, signs it with her CA private key, and serves it back to you.
- Your browser trusts the certificate because Nancy’s CA public key is in your trusted store.
- Nancy establishes a connection with acunetix.com and relays all the SSL traffic through her system.
SSL hijacking is very often used for legitimate purposes. For example, malware protection software installed on your computer probably uses SSL hijacking. If not, the software would not be able to protect you when you try to download malware using a secure connection. Some companies use SSL hijacking to control traffic in their internal networks, for example, to check what content their employees are accessing. Parental control software also uses SSL hijacking.
SSL Stripping
When you type an address in your browser, your browser first connects to an insecure site (HTTP). Then, it is usually quickly redirected to the secure site (HTTPS). If the website is available without encryption, the attacker can intercept your packets and force an HTTP connection. If you don’t notice that your connection is unencrypted, you may expose secrets to the attacker. This technique is called SSL stripping.

If Nancy wants to use SSL stripping to get your secrets:
- Nancy listens in on your connections to secure websites and intercepts them.
- Nancy modifies your initial web requests (they are sent using plain text). The server thinks that your browser is requesting to be served via HTTP.
- If the website is configured to serve content via HTTP, your data is sent in plain text and Nancy can read it.
Today, many websites use HTTP Strict Transport Security (HSTS) which means that the server refuses to provide content using an insecure connection. Such websites cannot be attacked using this method.
Other Methods Used for Eavesdropping
There are more methods used to compromise secure connections, including:
- SSL/TSL vulnerabilities: Older versions of SSL/TLS protocols are vulnerable to attacks that let black hat hackers decrypt the data. For example, CRIME or BEAST attacks.
- Session hijacking: If parts of the site are available via HTTP and other parts via HTTPS, an attacker may easily get the session cookie and impersonate the user. Session cookies may also be stolen if the website is vulnerable to Cross-site Scripting.
How To Detect and Prevent a Man-in-the-Middle Attack
There are many types of man-in-the-middle attacks and some of them very difficult to detect. The key to preventing them is to have as little trust as possible.
It is more difficult to prevent interception. If the attacker is able to access your network directly, if they compromise the destination server, or if they control network equipment that is used for your connection, there is not much that you can do. What you can do in such cases is choose a different communication route or make sure that encryption is unbreakable.
Here are some basic tips that may help you:
- Patch your system and use renowned anti-malware software.
- Don’t use public networks and/or hotspots for any sensitive activities.
- When connecting to your Wi-Fi, check if you are not connecting to a network with a similar name.
- Don’t forget to check the browser address bar and make sure you are using a secure connection.
- Click the lock symbol next to the address bar to get more information about the certificate.
- Install add-ons that help you detect SSL hijacking, for example, CheckMyHTTPS.
- Never send any sensitive information via email and do not trust any emails with sensitive information.
- Set up two-factor authentication wherever you can. Even if an attacker intercepts your data, they will have a hard time getting control of your Android or iPhone as well.
Does SSL Protect Against Man-in-the-Middle Attacks?
Some sources may say that SSL/TLS is enough to protect against MITM attacks. This is not true for the following reasons:
- The weakest link in a MITM attack is often the human. For example, if you don’t monitor the lock symbol on your browser address bar, you will easily fall for an HTTP stripping attack.
- Older versions of SSL/TLS may be vulnerable to MITM attacks. If the client or the server uses an older version of SSL/TLS, the attacker may be able to break the encryption.
- If the attacker compromises your computer or the server, they may tap the communication before it is encrypted or after it is decrypted.
- In the case of email, connections to servers may be encrypted but it is not as common as in the case of web connections. Also, email is stored on the server and often sent between servers in plain text.
How to Prevent MITM Attacks Against My Website?
Man-in-the-middle attacks are often facilitated by websites, even if your client and connection are safe. If you own a website, make sure that you regularly scan it for vulnerabilities, for example, using the Acunetix web vulnerability scanner (click here for a demo version). If you don’t, some vulnerabilities such as SQL Injection or code injection may let someone install malicious software on your web server. In addition, the Acunetix scanner also checks for SSL/TLS vulnerabilities that might let the attacker eavesdrop on connections to your web server, for example, CRIME, BREACH, and POODLE.
Frequently asked questions
In a man-in-the-middle attack (MITM), a black hat hacker takes a position between two victims who are communicating with one another. In this spot, the attacker relays all communication, can listen to it, and even modify it. Man-in-the-middle is a general term for many different types of such attacks that use different Internet technologies.
Man-in-the-middle attacks can be very dangerous for you. Malicious hackers can use MITM attacks to get your personal information for identity theft, to get your login credentials (for example, to gain access to your online bank account), to get your credit card number when you are paying at an online shop, and more.
Read how a totalitarian government tries to use MITM attacks to spy on the population.
Common types of MITM are: ARP spoofing (ARP cache poisoning), IP spoofing (IP address spoofing), DNS spoofing (DNS cache poisoning), HTTPS spoofing (IDN homograph attacks), SSL hijacking, and SSL stripping. You can learn how these attacks work by reading this article.
To prevent MITM, always patch your system to the latest version, don’t trust public networks (such as free Wi-Fi), check the Wi-Fi name that you connect to, check the address bar of your browser and the certificate, and use multi-factor authentication. If you own a website and want to protect your users, make sure that your website does not have any web vulnerabilities by using a web vulnerability scanner such as Acunetix.
Learn how Acunetix Premium protects your websites and web applications.
Get the latest content on web security
in your inbox each week.




