Acunetix includes the classification of vulnerabilities using CVE (Common Vulnerabilities Exposure), CWE (Common Weakness Enumeration) and CVSS (Common Vulnerability Scoring System).
The table below provides a quick overview of the main differences between the three standards and how they benefit Acunetix users.
| CVE | CWE | CVSS | |
|---|---|---|---|
| Full Name | Common Vulnerabilities and Exposures | Common Weaknesses Enumeration | Common Vulnerabilities Scoring System |
| What is it? | A dictionary of publicly known security vulnerabilities and exposures. | A community-developed dictionary of software weakness types. | A vendor-agnostic industry open-standard designed to convey vulnerability severity. |
| Main Benefit | Easier to share vulnerability data across different databases and tools. Different security tools can now “talk” to each other using a common language. | Provides a standard measuring stick for software security. | Helps determine urgency and priority of response when vulnerabilities are detected. |
| Solution | Provides a baseline for evaluating the coverage of an organization’s security tools. | Provides a common baseline for weaknesses identification, mitigation and prevention efforts. | Solves the problem of multiple incompatible scoring systems. |
| More information | http://cve.mitre.org/index.html | https://cwe.mitre.org | http://www.first.org/cvss |
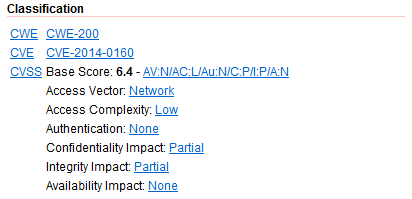
All the vulnerability alerts in Acunetix are categorized using CVE, CWE and CVSS. This categorization can be found within the Classification section in the Alert details.
Taking the Heartbleed bug as an example to illustrate the above, this particular vulnerability is listed under a specific CVE identifier of CVE-2014-0160. It is also classified under the more general CWE-200: Information Exposure weakness. In addition, it has been given an CVSS Score of 6.4.
With this in place, you can augment the information being provided by the Acunetix scanner and hence improve your ability and speed in responding to and mitigating software weaknesses and application vulnerabilities.
Get the latest content on web security
in your inbox each week.




