It all started a few months ago when I was visiting Lester Chan’s website looking for some information about one of his plugins. Lester Chan has written a good number of very popular WordPress plugins that are used by millions of people. Some of the most popular ones are WP-PageNavi, WP-DBManager, WP-PostRatings, WP-Polls and WP-PostViews.
It all started a few months ago when I was visiting Lester Chan’s website looking for some information about one of his plugins. Lester Chan has written a good number of very popular WordPress plugins that are used by millions of people. Some of the most popular ones are WP-PageNavi, WP-DBManager, WP-PostRatings, WP-Polls and WP-PostViews.
While visiting his website I noticed a blog post named ‘Code Injection Follow Up‘. Basically, somebody managed to gain access to his WordPress.org account and modify 2 of his plugins, introducing malicious code to both of them. The plugins that were affected are WP-Polls v2.60 (755,250 total downloads) and WP-PostRatings v1.50 (482,150 total downloads). A lot of people are using these plugins and I’m sure many of them were affected by this intrusion.
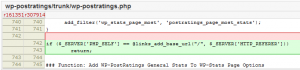
What did the attacker do? Here is a screenshot of the changeset in question (from WP-PostRatings. The other one is identical).
The code looks innocent at first as well as being very cleverly hidden inside the plugin code. The attacker is taking advantage of the links_add_base_url WordPress function and by manipulating the Referer header, it’s possible to gain PHP code execution. Pretty smart if you ask me.
These plugins were modified on 11/04/10 and Lester Chan fixed them on 02/14/2011. Therefore, for just over three months, people downloaded backdoored versions of these plugins. That’s a huge number of WordPress security threats!
Recently, WordPress made the following announcement:
Earlier today the WordPress team noticed suspicious commits to several popular plugins (AddThis, WPtouch, and W3 Total Cache) containing cleverly disguised backdoors. We determined the commits were not from the authors, rolled them back, pushed updates to the plugins, and shut down access to the plugin repository while we looked for anything else unsavory.
Again, the same story. Somebody somehow (maybe even WordPress.org was compromised, although we don’t know for sure if that’s the case) gained access to a popular WordPress plugins development account and inserted malicious code. The affected plugins are:
- AddThis v2.1.3
- 451,948 total downloads
- WPtouch v1.9.28
- 2,106,142 total downloads
- W3 Total Cache v0.9.2.2
- 537,594 total downloads
From what I can see, the plugin authors didn’t increase the version number when fixing the vulnerability. Therefore, if you have the versions listed above, it doesn’t necessarily mean that you are vulnerable, but I would still recommend downloading and re-installing the plugins to ensure your blog runs on a secure WordPress platform.
In my professional opinion, the keywords in the WordPress announcement were “cleverly disguised backdoors.”
In the following article, I will show you the changes the attacker(s) made to the three compromised WordPress plugins.
Get the latest content on web security
in your inbox each week.