On March 2, 2007 the following was posted on the WordPress blog:
Long story short: If you downloaded WordPress 2.1.1 within the past 3-4 days, your files may include a security exploit that was added by a cracker, and you should upgrade all of your files to 2.1.2 immediately.
Longer explanation: This morning we received a note to our security mailing address about unusual and highly exploitable code in WordPress. The issue was investigated, and it appeared that the 2.1.1 download had been modified from its original code. We took the website down immediately to investigate what happened.
It was determined that a cracker had gained user-level access to one of the servers that powers wordpress.org, and had used that access to modify the download file. We have locked down that server for further forensics, but at this time it appears that the 2.1.1 download was the only thing touched by the attack. They modified two files in WP to include code that would allow for remote PHP execution.
Basically, a cracker gained access to one of the WordPress servers and modified two files from the WordPress installation. One of these files is theme.php (located in the wp-includes) directory where the cracker inserted the following pieces of the code:
This modification introduced a system code execution vulnerability in the WordPress code.
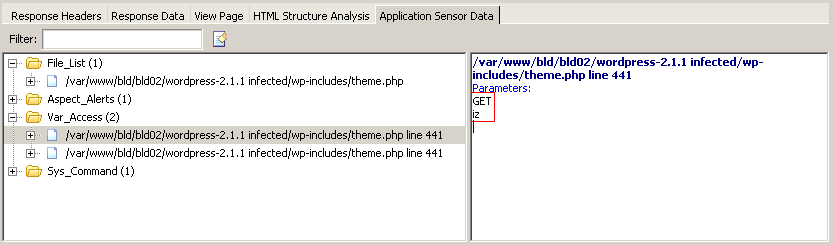
It was possible to read the contents of the /etc/passwd file using an URL like:
http://host/wordpress-2.1.1 infected/wp-includes/theme.php?iz=cat+/etc/passwd
A vulnerability like this one cannot be detected with a typical black box vulnerability scanner. The cracker introduced a new input parameter named ‘iz’ and the value of this parameter is sent through the ‘passthru’ function (the PHP passthru function will execute an external program and display raw output). This input parameter is not directly linked from anywhere; therefore a black box scanner will never know about this parameter and will not test it.
This is where the AcuSensor Technology comes into place; it builds a list with all the inputs from the application (by parsing the source code and intercepting variable access). E.g. on PHP it intercepts all the access to $_GET and $_POST arrays and build a comprehensive list with all the possible inputs. Therefore, when scanning the application with AcuSensor Technology enabled, the ‘iz’ input parameter will be discovered and tested (as shown in the Screenshot 2).
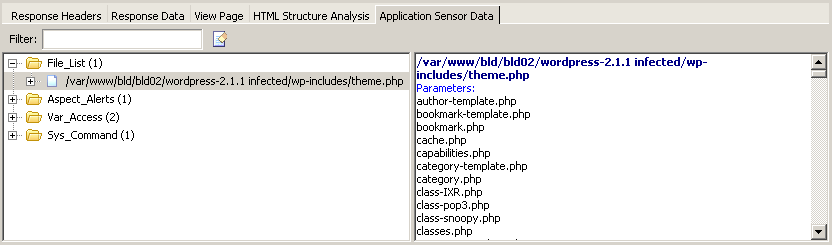
Even more, the AcuSensor Technology will build a list with all the files in the application directory, therefore allowing us to scan for files which are not directly linked from the website. If an attacker gains access to the website and creates a backdoor file in the application directory, this file will be found and scanned if AcuSensor Technology is enabled.
Because the ‘iz’ parameter is now found, the scanner can test it and report the vulnerability, as shown in the screenshot below.
Get the latest content on web security
in your inbox each week.