An
An .htaccess file is a configuration file which provides the ability to specify configuration settings for a specific directory in a website. The .htaccess file can include one or more configuration settings which apply only for the directory in which the .htaccess file has been placed. So while web servers have their own main configuration settings file, the .htaccess file can be used to override their main configuration settings. Each directory can have its own .htaccess file.
Below are some examples that show how .htaccess files can be included in multiple directories, each responsible for the configuration of the directory it is saved in.
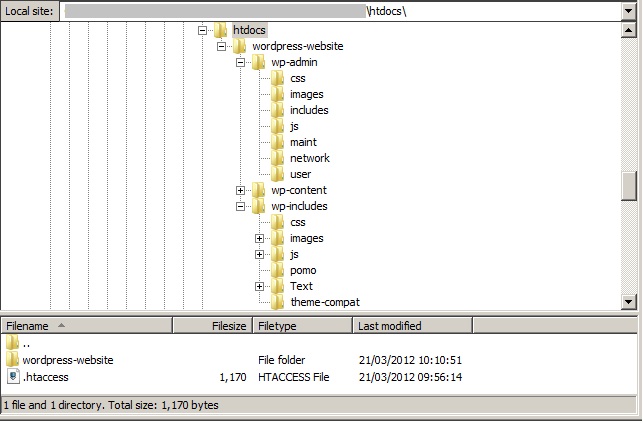
The directories marked with red in the below screen shot contain an .htaccess file.
The next example shows the .htaccess file in the root or main website directory. In the htdocs directory (or root directory), you can host multiple websites. Thus, the .htaccess file controls who can access this root directory and eventually gain access to all the subdirectories. The below example is for the wordpress-website directory.
In the next example, the .htaccess file is included in the wordpress-website directory which controls who can access the wordpress-site directory. For instance, someone that has access to the htdocs directory might not be able to access the wordpress-site directory due to authentication restrictions.
 The same happens in the next example, where the
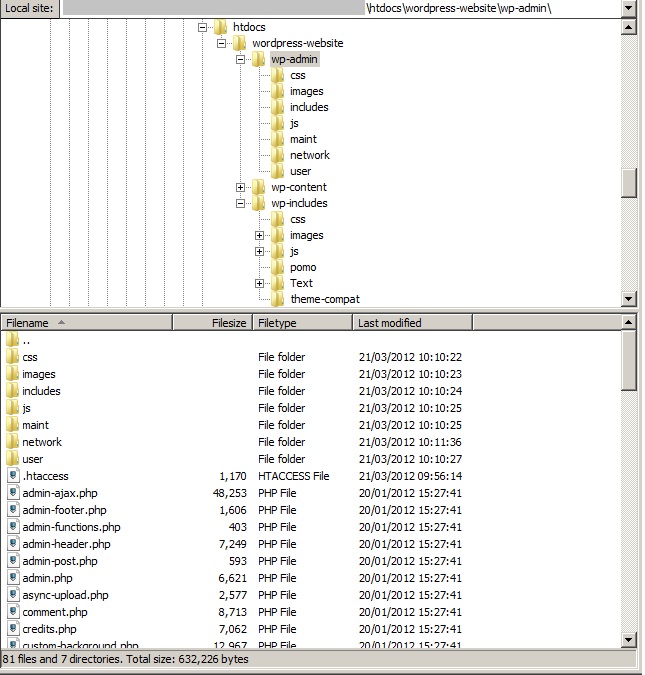
The same happens in the next example, where the .htaccess file controls who can access the wp-admin directory. Again, a user might be able to access the wordpress-website directory but not the wp-admin directory.
In the below examples we explain how .htaccess files can be used to control access to directories. .htaccess files can also be used to specify other configuration properties and not just for authentication and access control.
Security Precautions When Using .htaccess Files
When writing an .htaccess file, you must be careful of how directives and configuration settings are used. A malicious user can easily take advantage of an insecure .htaccess file configuration and gain unauthorized access to your website. In the example below, we will explain how a malicious user can bypass an insecure .htaccess file configuration and gain access to the website.
When configuring the .htaccess file, the limit directive is sometimes used by the web master. The limit directive, as the name implies, limits the HTTP verbs or methods to be used for the specific HTTP request. The most common HTTP methods are GET and POST. An example of an .htaccess file that uses the limit directive can be found below:
AuthUserFile /etc/httpd/.htpasswd
AuthType Basic
AuthName “restricted”
Order Deny,Allow
Deny from all
<limit GET POST>
Require valid-user
</limit>
Satisfy anyIn this scenario the limit directive only allows GET and POST HTTP verbs or methods to be used. However, according to the Request for Comment (RFC) 2616, some HTTP verbs are triggered or handled in the same way. For example, the GET HTTP method can be handled in the same way as the HEAD HTTP method. Thus an attacker in this scenario, where HTTP requests are limited to GET and POST HTTP methods only, can easily use the HEAD HTTP method which is not set in the <limit> tag in order to bypass the authentication mechanism. This attack is called HTTP Verb Tampering.
Typically, in the .htaccess file the web master also configures custom error pages or hardcoded URL redirects. Custom error pages are used to hide a default error page which might contain critical information about the website. If a malicious user manages to gain unauthorized access on the .htaccess file, the attacker can replace the custom error page redirects with redirects to malicious websites. Such redirects will cause serious issues to the end-users since the injected redirects by the hacker might take the visitor to malicious websites that serve malware, which could mean the user is infected. From such redirects, a malicious user is also able to steal visitor’s sensitive information.
Get the latest content on web security
in your inbox each week.