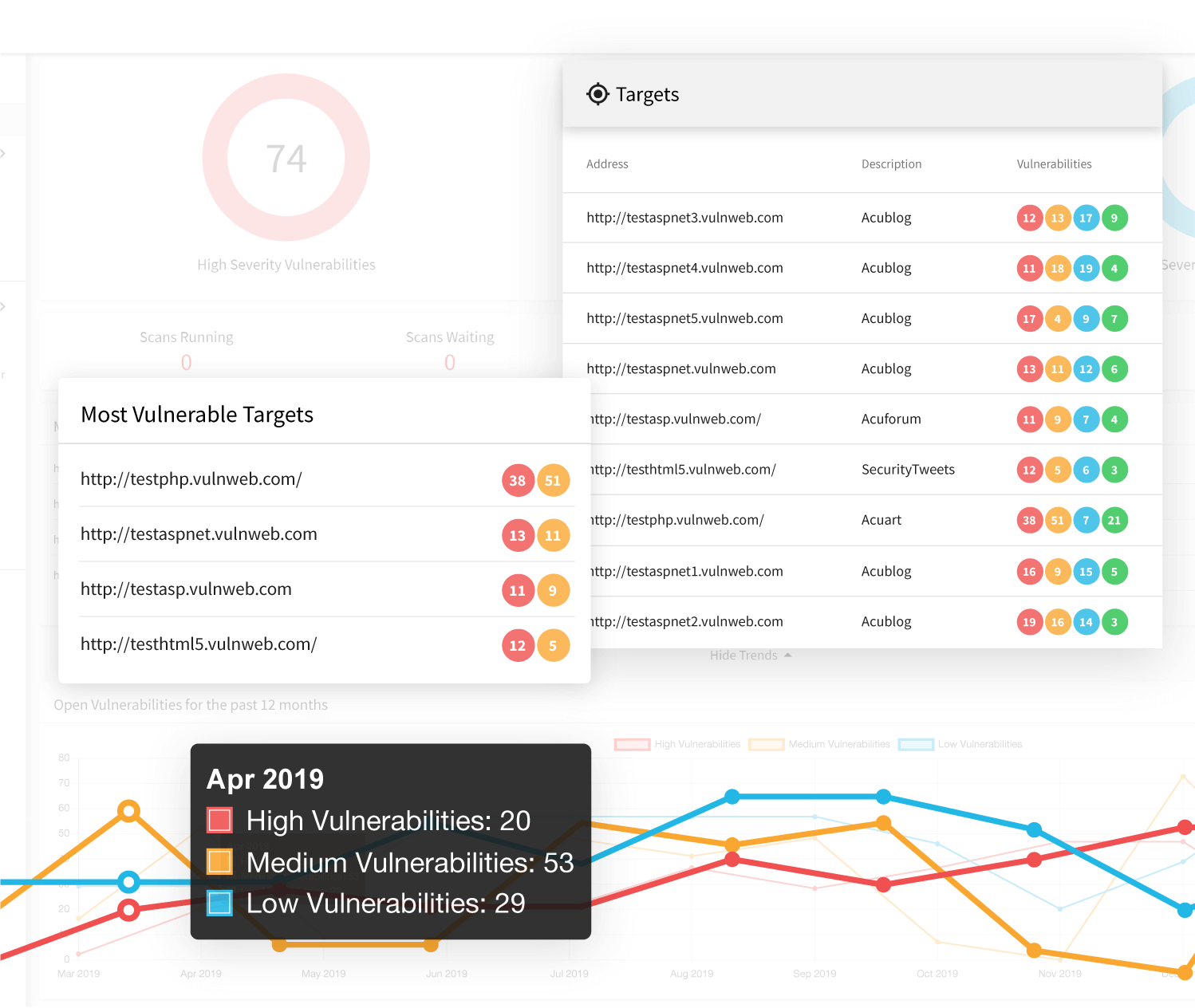
Protect Your Operating System with Holistic Vulnerability Management
With the rise in web applications, more opportunity has emerged for malicious hackers that seek to cause havoc. There are many network vulnerabilities that exist in TCP/IP, so detection is important. But not all network vulnerability scanners are alike. The integrated OpenVAS scanner works with Acunetix Premium to provide function and reliability for all of your security testing needs.
Even the most advanced firewalls, SSL, and hardened networks are not able to keep your networks secure. For attackers, there are many points of entry to trespass and access your information, and your internet protocol (IP) communications is one of them.
IP Vulnerabilities
In the case of ARP spoofing, a hacker sends false ARP (address resolution protocol) messages over a local area network. This is problematic, to say the least as the malicious MAC address will connect to the IP address of the legitimate computer and begin receiving all data intended for that IP address.
Port Scanning is another way that malicious actors can gain access to your network. By using a port scanner to search all open ports and their devices, your entire IP network configuration can be mapped out. That is like giving a stranger the keys to your building.
The Internet Protocol (IP) facilitates the transmission of information via data packets. Once information is distributed into packets, IP initiates a list of the possible pathways the packets may take to get to their final destination. Unfortunately, at this stage, the network is at its most vulnerable. Attackers can breach the system and gain access to the packet routes, opening up the potential that routes could be modified or even that data could be read. This is what is known as a source route attack.
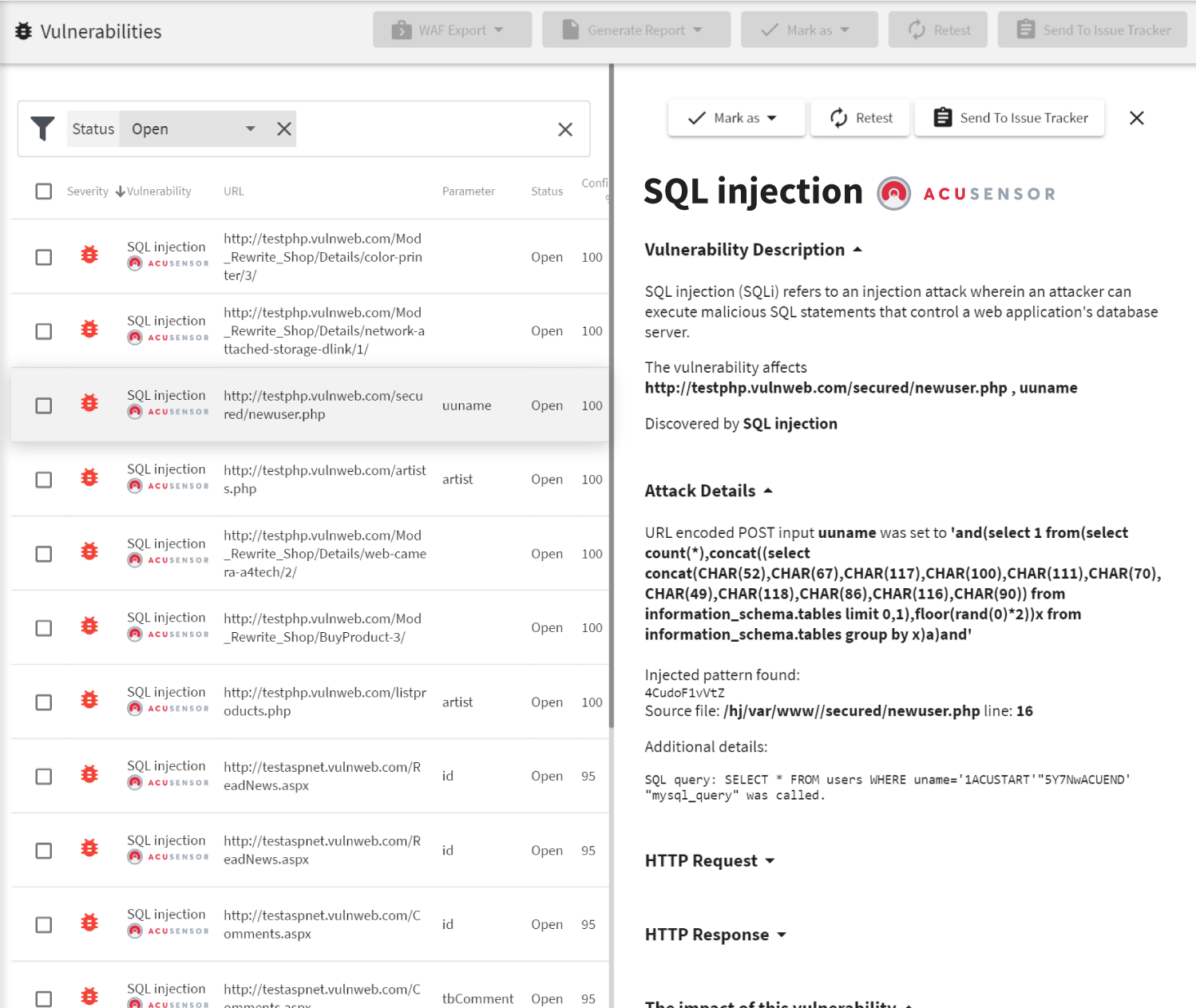
Looking Ahead with Acunetix
New vulnerabilities emerge every day, so make sure you are prepared with advanced vulnerability scanning and security tools from Acunetix. Our combination of black-box and white-box internal scan testing eliminates the occurrence of false positives and helps guarantee your network security.
Frequently asked questions
The term IP vulnerability scanner is used to describe network scanners because they focus on TCP/IP stack vulnerabilities (IP, TCP, and UDP protocols). One of the best network IP vulnerability scanners available on the market is the open-source OpenVAS.
The most common type of IP network vulnerability is open ports. Many administrators expose services that should not be accessible from the outside. Open ports may cause data breaches if the attacker can reach a database from outside and the database is not protected with authentication.
Read about the consequences of exposing databases to the Internet.
More and more websites and web applications are hosted in the cloud. With the exception of manually opened ports, there are few network vulnerabilities that may affect cloud hosting because it is managed centrally. That is why network scanning became less important than web scanning but is still recommended.
Read more about the basics of web security and its importance.
When you integrate Acunetix with OpenVAS, you see all network issues and web issues together and can manage them together. To integrate Acunetix on-premises with OpenVAS, all you need to do is to follow the guide below. If you use Acunetix Online, you don’t need to install or configure anything.
Learn how to install OpenVAS and integrate it with Acunetix on-premises.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox