File inclusion vulnerabilities are a major cause for concern within web applications since successful exploitation of such a vulnerability may lead to remote code execution (RCE). Once an attacker gains the ability to execute arbitrary code in an application, it’s much easier for that attacker to escalate their attack and do more damage, such as, for example, “pivoting” to other hosts on the internal network in order to steal sensitive data.
File inclusion vulnerabilities are usually not difficult to fix, but finding them in large codebases could be challenging without the right tools. Acunetix is a web application vulnerability scanner and file inclusion is one of the myriad of vulnerability test that it performs.
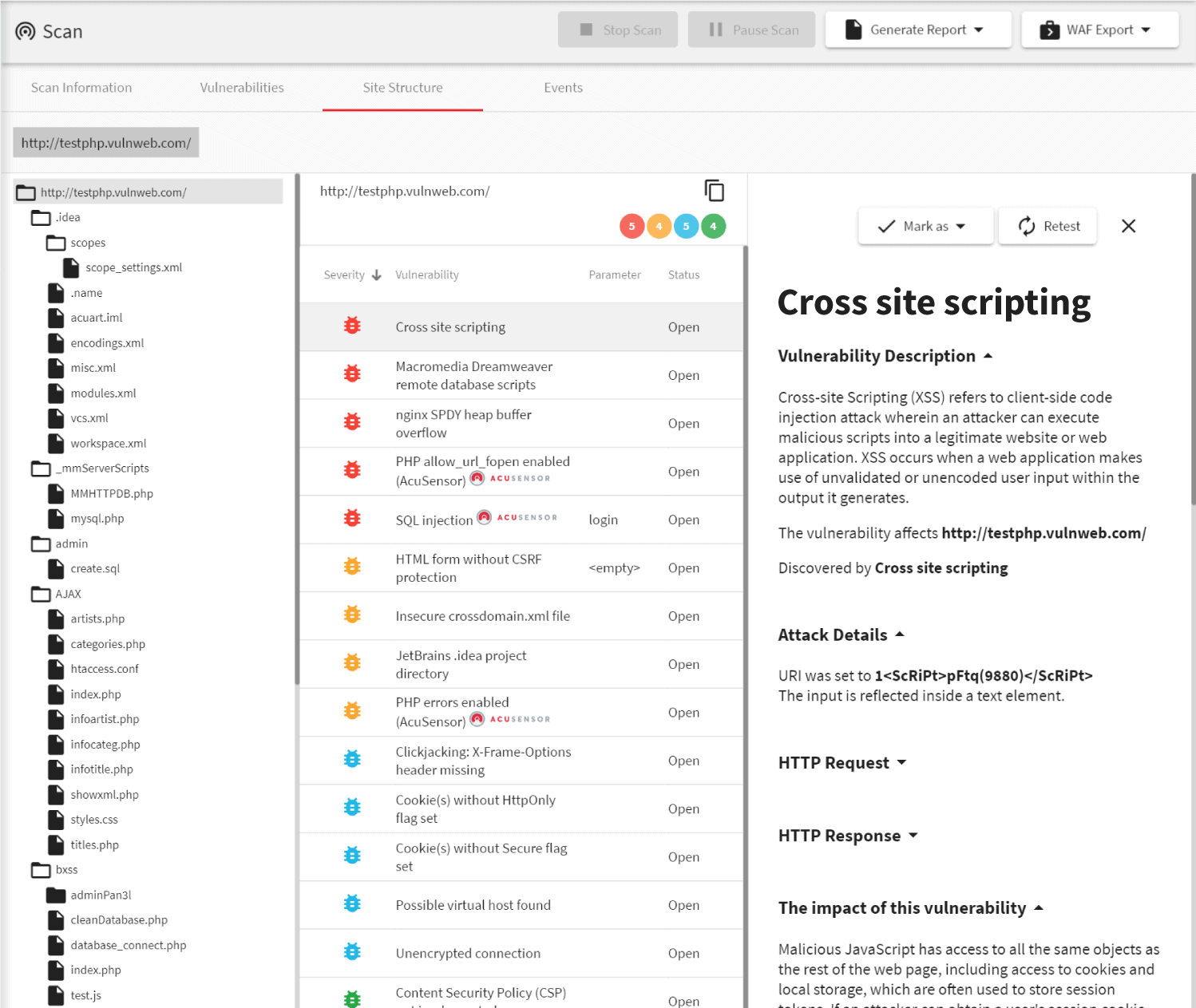
Beyond Low-Hanging Fruit
The Acunetix file inclusion vulnerability scanner acts as an LFI vulnerability scanner that tests for local file inclusion (LFI) and an RFI vulnerability scanner testing for remote file inclusion (RFI). While many file inclusion vulnerability scanners can find low-hanging file inclusion, Acunetix goes well beyond the basics thanks to its advanced crawler and JavaScript engine called DeepScan. Thanks to DeepScan, Acunetix also has full support for modern single-page applications (SPAs) and can understand and fully test applications that rely on JavaScript frameworks like React, Angular, Ember, and Vue. This means Acunetix can understand an underpinning RESTful API when crawling a SPA. Since Acunetix understands way more than JSON and XML, it can build a correct input scheme (an internal representation of web application input), which it may then rigorously test for both local file inclusion (LFI) as well as remote file inclusion (RFI).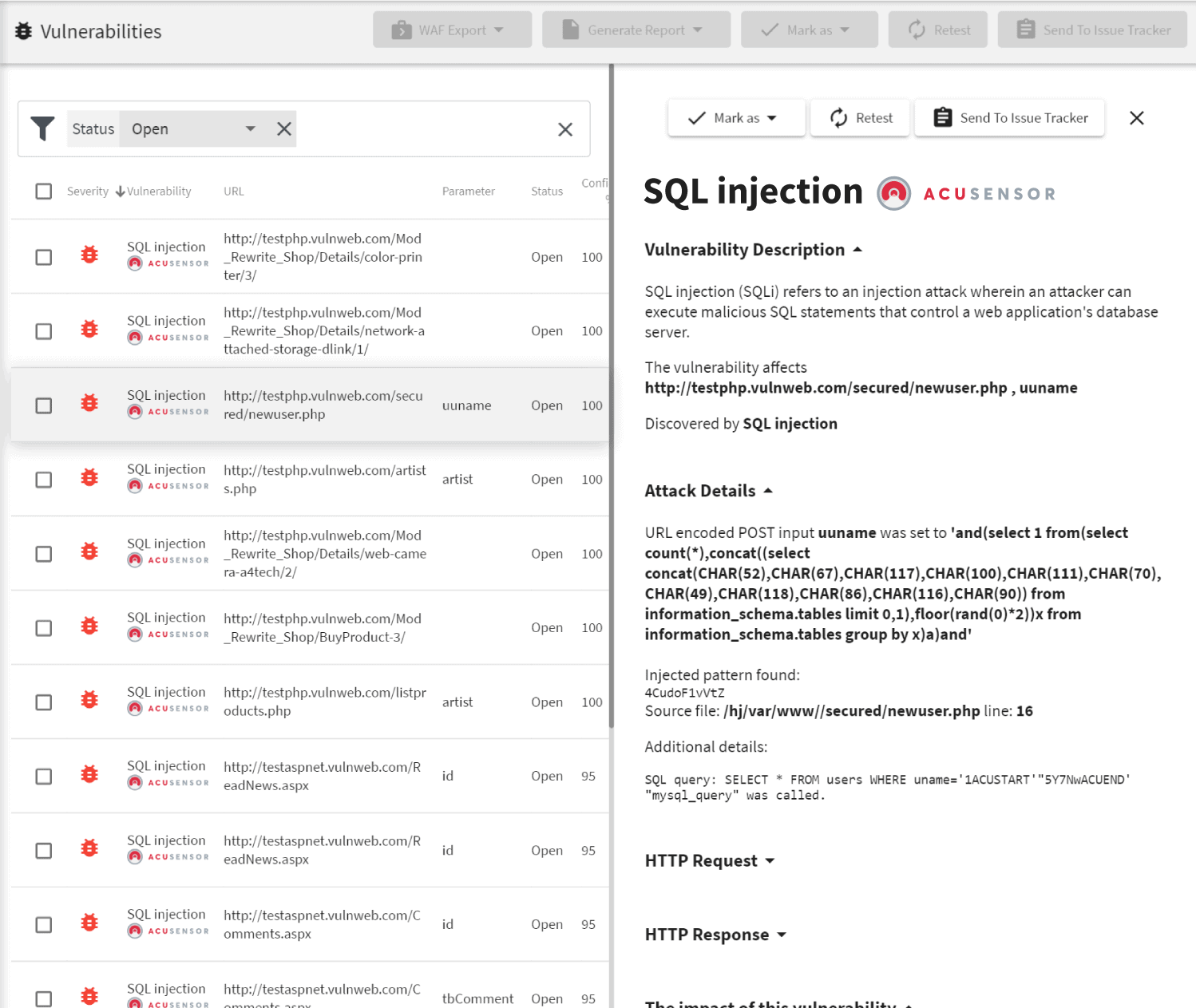
Runtime Source Code Analysis
In addition to being a fully automated black box (no knowledge of backend code) file inclusion vulnerability scanner, Acunetix also provides AcuSensor as part of its standard offering. AcuSensor is a an optional sensor for Java, ASP.NET, and PHP applications that can easily be deployed on the application back end to analyze source code while it is in execution by the scanner. This type of testing is known as gray box testing since it combines the best of both worlds from black box testing and white box testing. When testing for file inclusion vulnerabilities, Acunetix AcuSensor increases the accuracy of a scan since it has access to the code on the back end. With AcuSensor, the Acunetix file inclusion vulnerability scanner may also test pages that would not otherwise be discovered via crawling thanks to the AcuSensor back end crawl technology.
Customizable Scope
When scanning large applications for file inclusion vulnerabilities, it may be desirable to divide the scanning of the application up into smaller segments or scopes. A typical example of this would be when different development teams would be working on different parts of a large web application with different release cycles and therefore different scanning schedule requirements. Acunetix makes customizing the scope of a file inclusion vulnerability scan easy and painless. There are several ways to restrict the scope of a file inclusion vulnerability scan – you may choose to exclude pages you don’t want to scan manually, or for more advanced users, Acunetix also supports excluding pages based on regular expressions. So don’t sit idle on file inclusion vulnerabilities. Get the most out of your web security efforts with Acunetix.Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox