Acunetix as Automated Penetration Testing Software
To effectively assess the state of web application security, businesses need offensive security (ethical hacking) solutions – penetration testing software. As part of this approach, you should use an automated web vulnerability scanner and perform manual web penetration testing. Both steps are needed because penetration testers are too valuable to spend time on issues that can be found automatically and vulnerability scanners cannot discover all types of security vulnerabilities (for example, business logic issues). Vulnerability scanners are often considered as pentesting tools because they are used by security professionals in the first stage of a comprehensive web security assessment. Consider using Acunetix as your initial penetration testing tool. Acunetix is renowned for its high performance (engine written in C++) and a low rate of false positives. It is available for Microsoft Windows, Linux, and macOS operating systems as well as an online (cloud) solution.

Automated Penetration Testing Tool
If you work as a pen tester or ethical hacker, Acunetix can help you in several ways, depending on your requirements and workload.
- You can run Acunetix manually before beginning a penetration test to find common web application vulnerabilities such as SQL Injections, Cross-site Scripting (XSS), and more (including most OWASP Top-10 vulnerabilities as well as misconfigurations).
- After you run an Acunetix scan, in many cases you get proof that the vulnerability is real. You can then focus on other vulnerabilities and retest manually or you can simply trust Acunetix and spend your time searching for more complex issues.
- If you don’t want to rely on automatic testing at all, you can use the Acunetix engine to crawl the web application and map its entire structure. You may then manually test the discovered structure.
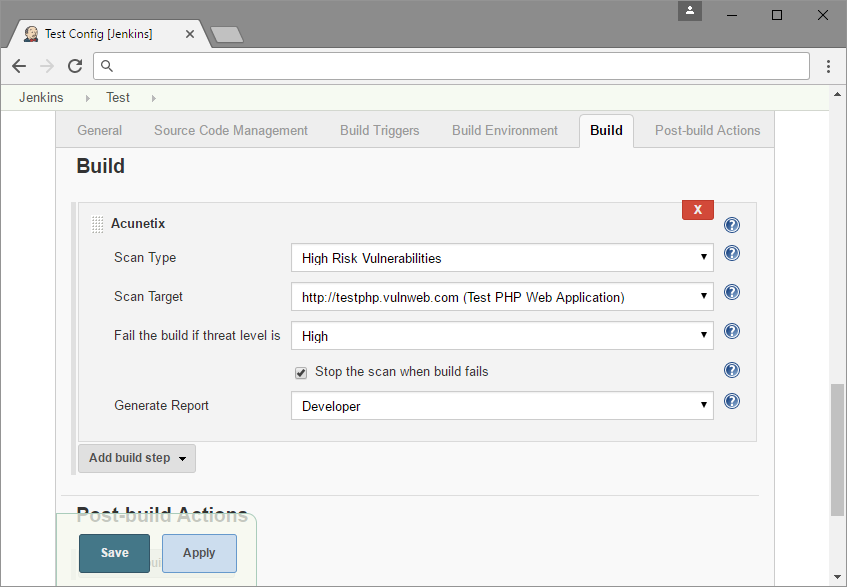
More Than Web Vulnerability Scanning
Acunetix started out as a simple vulnerability scanner but grew into a full-fledged vulnerability assessment and vulnerability management solution with extensive integration options including an API that you can use to build your own integrations.
- You can set up Acunetix to work in real-time within your SDLC. For example, an Acunetix scan can be triggered by Jenkins with every build.
- Acunetix can be used with your existing issue trackers such as Jira, GitLab, and more. This way, your security team can manage cybersecurity vulnerabilities outside of Acunetix along with all other issues.
- Acunetix can work with other security tools. For example, you can use Acunetix to set up temporary web application firewall (WAF) rules before your team can fix the vulnerability.
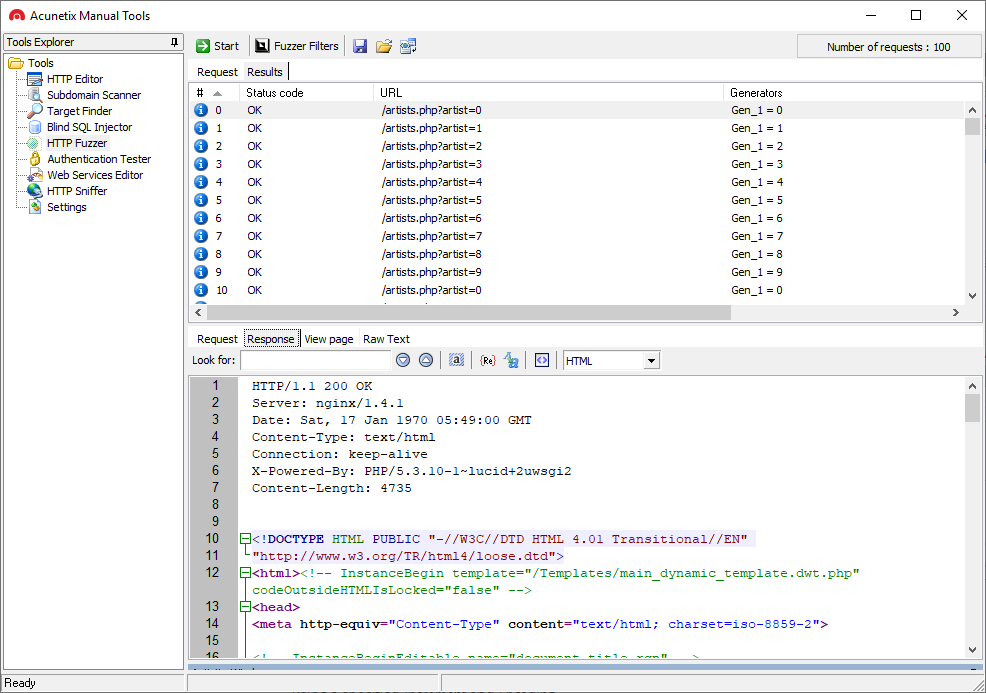
Further Manual Information Security Testing
In addition to an Acunetix scan, you can and you should follow up with further manual tests done using command-line and GUI-based penetration testing tools.
- While Acunetix tests for weak passwords using its own or supplied dictionary, you may attempt additional manual password cracking, for example, using a password cracker such as John the Ripper or THC Hydra.
- Acunetix does not test WiFi security. Therefore, you may need to use other tools, such as aircrack-ng, to check for example for WEP/WPA vulnerabilities.
- For further manual web and network traffic tests, you can use free manual pentesting tools and open-source tools such as packet analyzers, sniffers, brute force tools, testing frameworks, open port scanning tools, network mappers, and more. Some examples of such penetration testing tools are: Kali Linux, Zed Attack Proxy (ZAP), w3af, Nmap, Metasploit, Wireshark, Burp Suite, sqlmap, and more.
Frequently asked questions
The term penetration testing software is used to describe any software that can be used for performing manual or automated penetration tests. This includes network security and web security tools as well as many others. Vulnerability scanners are considered automated penetration testing software.
There are many free and professional penetration testing tools. These tools include automated vulnerability scanners like Acunetix. They also include manual tools like attack proxies (e.g. Burp Proxy), password crackers (e.g. John the Ripper), exploit frameworks (e.g. Metasploit), or even complete operating system distributions (Kali Linux).
Acunetix also provides simple free manual penetration testing tools.
You should do both. Vulnerability scanning is considered as automated penetration testing or as initial penetration testing. A vulnerability scanner can find 99% of vulnerabilities, but not all of them. That is why it is useful to follow up with additional manual penetration testing.
Read about the differences between vulnerability scanning and penetration testing.
You should do both. Vulnerability assessment is the stage that follows vulnerability scanning and penetration testing. A professional product like Acunetix first finds all vulnerabilities. Then it assesses their potential impact based on the severity of the vulnerability and the importance of the business asset.
Read about the differences between penetration testing and vulnerability assessment.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox