Web site security is the most overlooked aspect of securing data. We’ve all heard the term ‘hacker’ before and the damage they can do to financial institutions, retailers and other large corporations.
As of March 2016, Google reports that over 50 million website users have been greeted with some form of warning that websites visited were either trying to steal information or install malicious software. In March 2015, that number was 17 million. The financial impacts of this are of course enormous. A recently published report titled the ‘2016 Cost of Data Breach Study: Global Analysis’ has suggested that the average cost of a data breach continues to climb, now reaching an average of $4million per breach, or $158 per record from a survey of 383 companies worldwide. This represents a 29% increase in the space of 3 years.
Besides the dangers of a data breach itself, there is also the risk of reputation and credibility loss to those who fall prey to an attack on their web site security. In addition, a hacker’s motivations are becoming not only financial however, but also political. So overall, hackers can be hugely damaging to a business or institution, so unless web site security is a continuous effort, your organization could become the target of malicious attacks.
As a result, the industry has increased their efforts to improve their web site security, using web vulnerability scanners, penetration testers and therefore better protecting their sensitive data. But has it been enough?
A report compiled by Acunetix over a the period 2015 and 2016 shows that web app vulnerabilities have rapidly increased as companies demand faster web application release cycles to satisfy staff and customers. Web application vulnerabilities are dangerous for organizations as they risk not only brand and reputational damage, but data breaches and the major fines associated with these. The findings continue to reaffirm the widely held understanding that the web application vector is a major, viable and low-barrier-to-entry vector for attackers; be they financially motivated, “hacktivists”, nation-state attacks or threat actors.
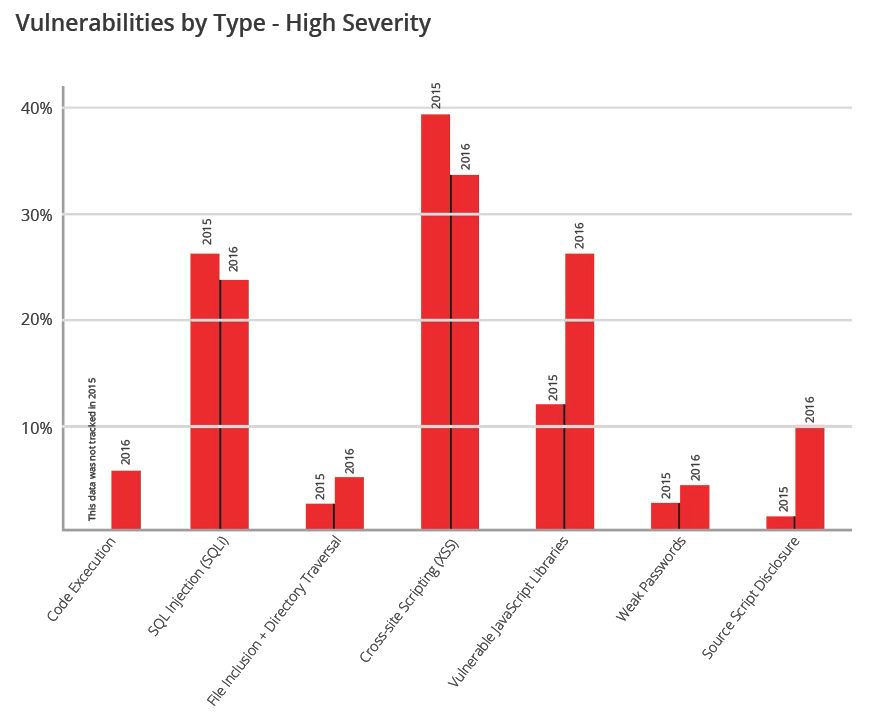
The threat landscape is changing—the web stack, has evolved to serve up rich experiences directly within the browser. As a result of the versatility and platform agnosticism that web applications provide, web
applications and web services are ever increasingly replacing legacy applications, and as a consequence, widening attackers’ exploitation opportunities; especially since traditional network-layer-only security controls such as firewalls and signature-based intrusion prevention and detection systems (IPS/IDS) have little, or no role to play in detecting and stopping an attack occurring via the web application vector.
Keeping yourself informed about web site security is one step in the right direction
Acunetix offers a series of articles, blog posts and up-to-date news on all that encompasses web site security. In the web security blog you can also find information on the latest web site security concepts and the most important web attacks, such as SQL injection & Cross-site scripting. In addition to explaining how web attacks work, we will also provide information on how to find and fix these vulnerabilities.
Subscribe to our web site security blog to get up-to-speed with the basics on web site security and to ensure you you have all the knowledge required for your web applications to remain hacker-proof.




