A comprehensive cyber security audit involves assessing security policies, security controls, and potential threats related to all information technology assets. That includes websites and web applications. While some parts of the audit must be performed manually by security auditors, Acunetix can partially automate the web risk assessment process. It assesses the security of your web assets by performing vulnerability scans to find known web vulnerabilities. It also helps you find other information security issues such as access control weaknesses, misconfigurations, or lack of certain security mechanisms. Additionally, if the IT security audit is performed to meet compliance requirements, Acunetix can generate audit reports for security compliance.
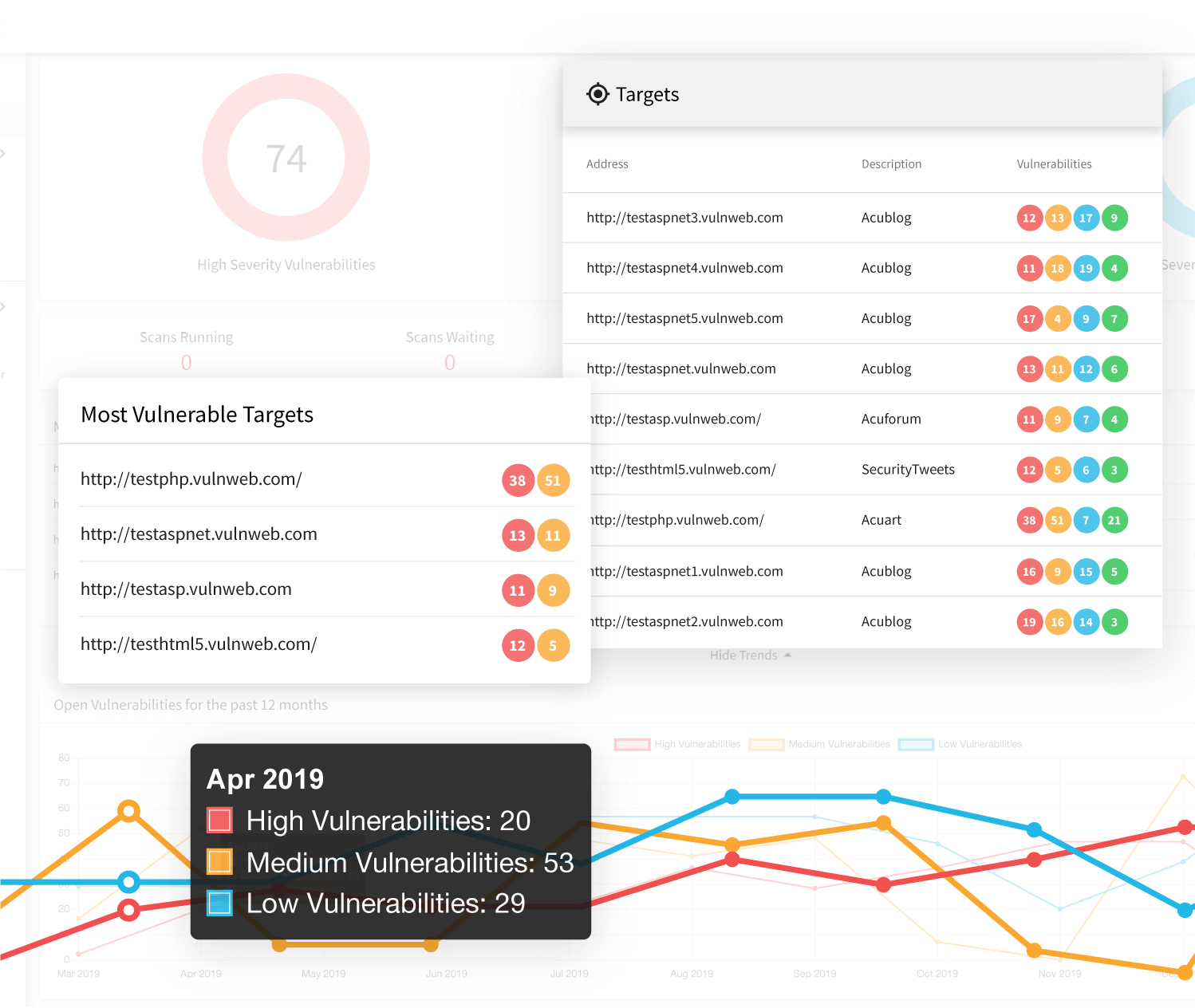
Finding and Assessing Known Vulnerabilities
Highest security risks associated with web assets come from web vulnerabilities. Cyber attack techniques such as SQL Injections or Cross-site Scripting (XSS) pose a big threat to data security and can lead to full compromise of operating systems. A key part of every information security audit is checking whether the IT environment is not vulnerable to such attacks.
- Acunetix is able to detect and provide details on thousands of web vulnerabilities. It does not just rely on signatures but actually checks if the attack is possible. An Acunetix scan is not intrusive and it poses no danger to information systems.
- Unlike some other security solutions, Acunetix is built to scan dynamic, complex web applications. It can enter areas that other products might miss. It can even enter protected areas if you provide suitable access control credentials.
Extensive Security Threat Assessment
In the case of cybercrime, several simple attack techniques can be chained together to lead to full system compromise. For example, an attacker may first use an SQL Injection, then privilege escalation, and finally, after getting control of your operating system, install dangerous malware such as ransomware. That is why it is important for a security assessment tool to provide information about potential consequences. With the right information, the most severe security issues may be addressed first and fixed quickly.
- Acunetix assesses the potential impact of vulnerabilities and gives them a severity rating. In addition, it provides details for further penetration testing by security professionals as well as fixing.
- In addition to known vulnerabilities, Acunetix also informs you about configuration issues or the lack of certain security protocols such as the content security policy. While these are not direct issues, they may have an impact on the security posture.
- After the security experts complete the audit and vulnerabilities need to be addressed, Acunetix helps you manage vulnerabilities by supporting integration with issue tracker software such as Atlassian Jira, GitLab, GitHub, Microsoft TFS, Mantis, and Bugzilla.
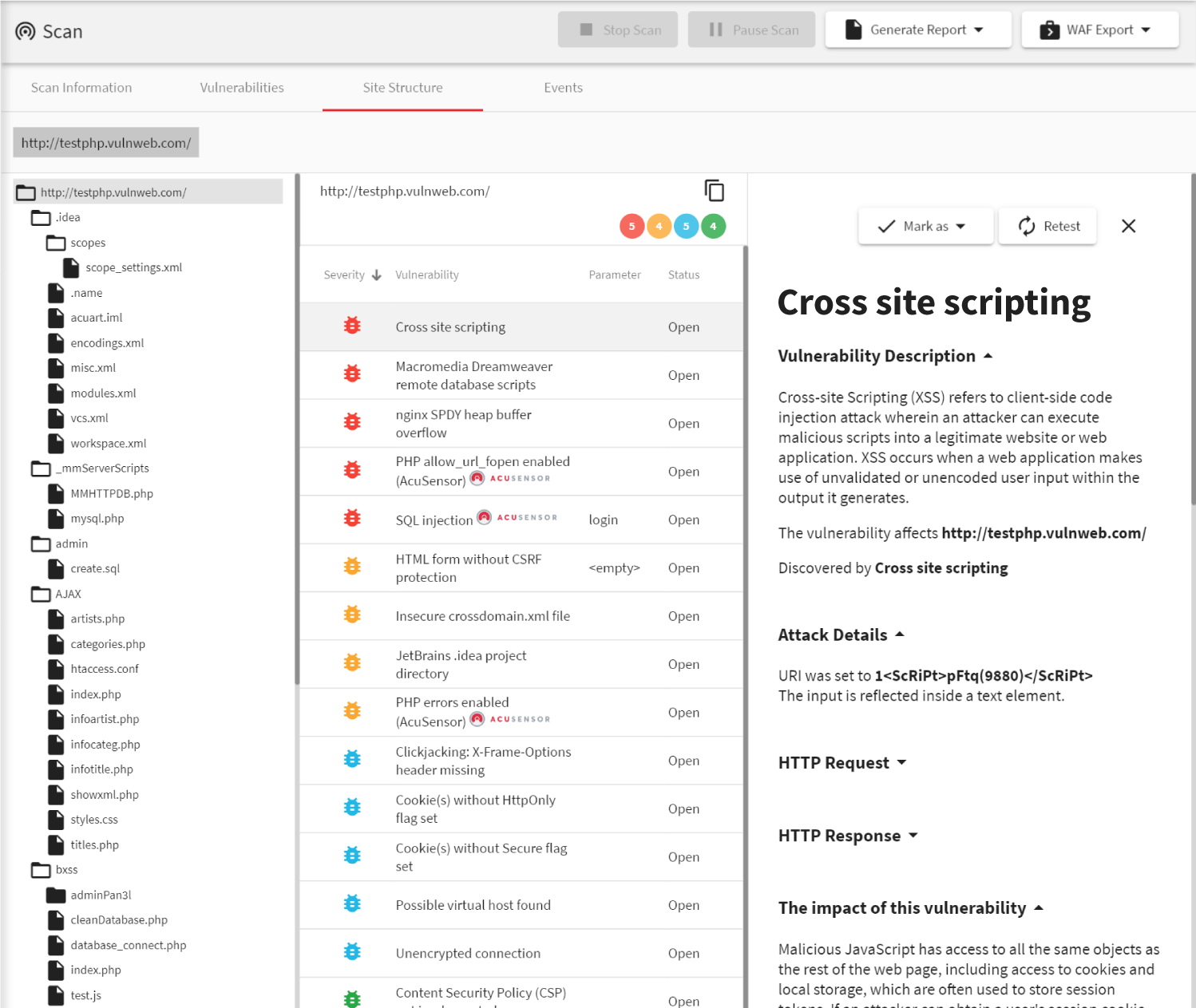
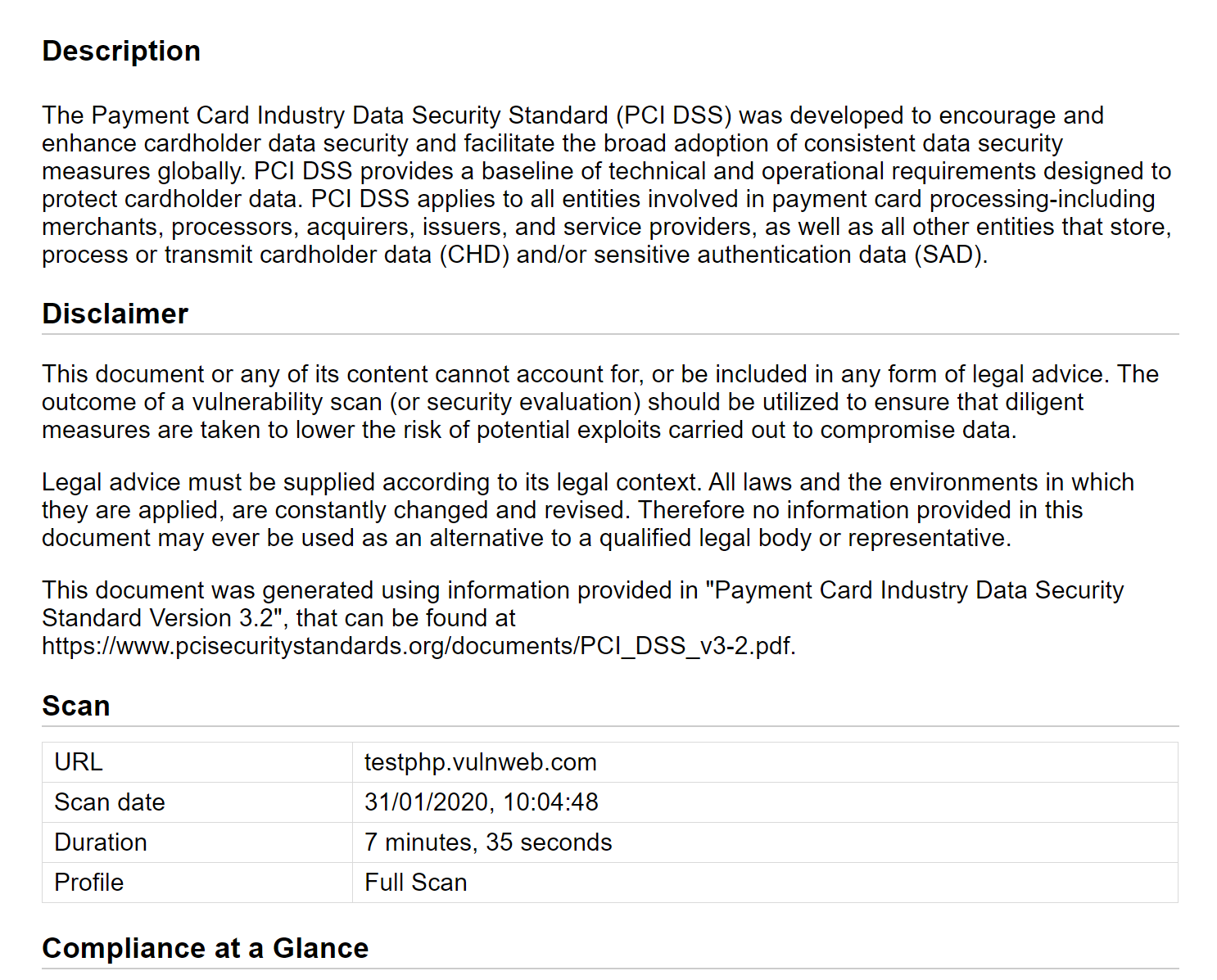
Comprehensive Reporting Capabilities
The key aspect of every security audit is reporting. This is especially important if the audit is meant to verify compliance. The Acunetix reporting engine has several built-in reports for different purposes including compliance purposes.
- Acunetix provides out-of-the-box reports for the following compliance standards: PCI DSS 3.2, HIPAA, ISO 27001, CWE 2011, NIST SP800 53, Sarbanes Oxley, STIF DISA, WASC Threat Classification, and OWASP Top 10.
- The Acunetix Executive Summary report can be used to quickly assess the security of your web assets and know where to focus team efforts to improve the security posture.
- To facilitate fixing vulnerabilities, developers can use the Developer Report. It provides information on the vulnerabilities together with remediation examples and best practice recommendations for fixing the vulnerabilities.

We utilize Acunetix to more thoroughly assess internet-facing websites and servers. Acunetix helps us identify vulnerabilities in conjunction with other vulnerability scanning applications. Acunetix has been a more reliable application when discovering / determining different types of malicious code injection vulnerabilities (SQL, HTML, CGI, etc).